A major flaw in Android operating systems between version 5.0 and 5.1.1 was revealed last week. University of Texas security researcher John Gordon posted information on the hack, along with a video of him using the exploit to reach the main screen of a locked phone.
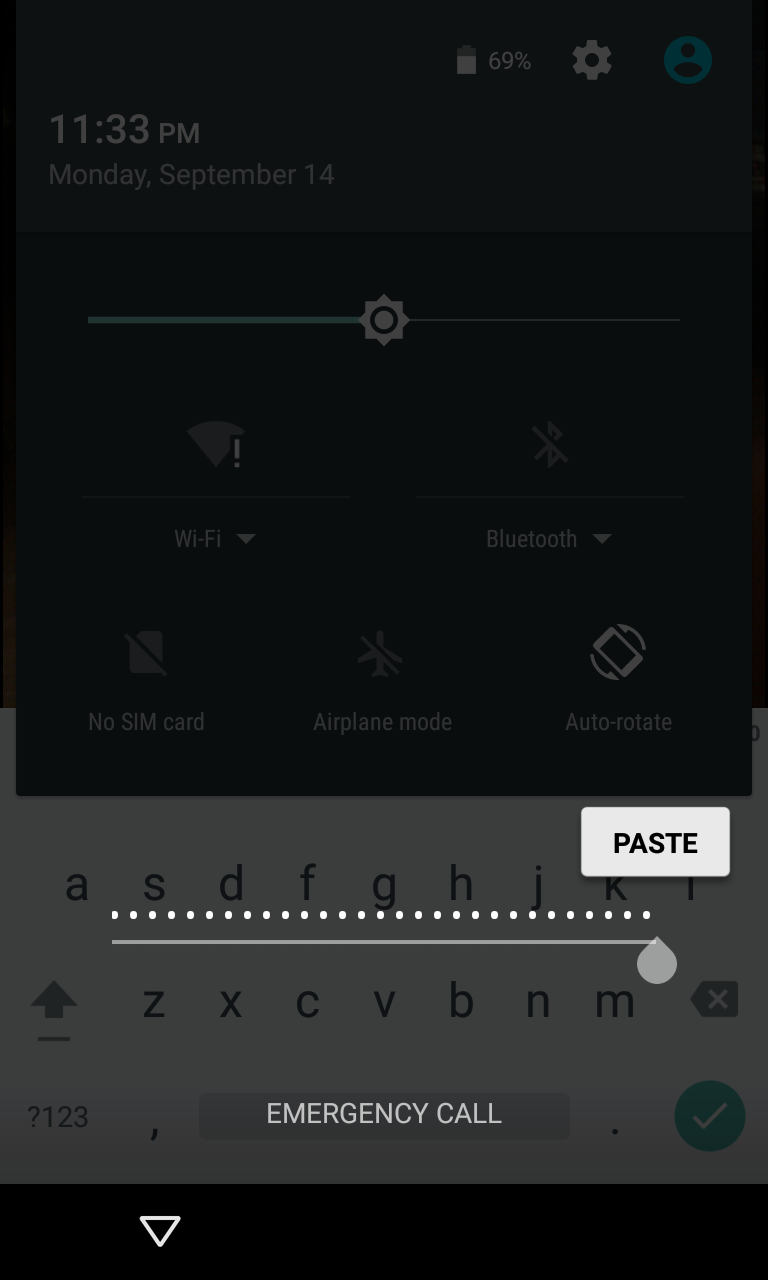
The hack itself involves exploiting a buffer overflow in the lockscreen of Android 5.0 through 5.1.1 phones. Users first bring up the emergency call window, which is accessible on any locked Android phone. Once in this screen, the user inputs an unusually large amount of text, such as a couple dozen pound signs. Once a large enough number has been submitted, it is copied into the text buffer.
The user then opens the camera application and pulls down the status bar to access the settings menu. Doing this results in a password input box, to which the excess text is pasted. The camera app then crashes and dumps the user to the desktop screen, unlocking the phone.
While a patch for this flaw was released last week, it still must be passed along to users through their phone vendor. As Android updates often take time to trickle down to end users, it is expected that this exploit will live on in the wild for some time.






