This year, the Open Web Application Security Project (OWASP) released its Top 10 2017 project for public review. There were two vulnerability updates to this year’s 14th release of OWASP, and although they were added to raise awareness on security risks in applications, one company is calling a movement for removal and replacement of one of the additions, OWASP Top 10-A7.
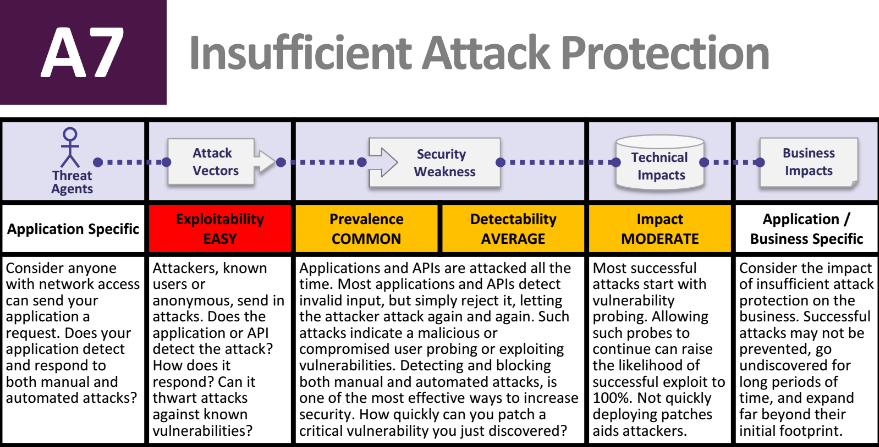
Synopsys, a company committed to making OWASP a data-driven project, said that the release candidate for the 2017 revision — A7 Insufficient Attack Protection — is “an inappropriate and potentially dangerous addition to the 2017 OWASP Top 10 Application Security Risks list.”
According to a blog post by Jim Ivers, vice president of marketing at the Synopsys Software Integrity Group, one of the new vulnerabilities in the OWASP Top 10 2017 list is a “point of contention and represent a slippery slope departure from the Top 10’s original tenants of risk management,” he wrote.
“It is the position of Synopsys that software security technologies emerge and evolve rapidly. Therefore, it is prudent to resist including any elements that prescribe security controls, particular security testing, or particular security testing products in the Top 10 Application Security Risks list—as presented in the new revision. We believe that such prescriptive language may induce organizations to rely too heavily on any one technology; thus, leaving themselves vulnerable to attack, which is contrary to the spirit and intent of the list,” wrote Ivers.
Synopsys prepared an article as an official response to call for review of the latest revision of the OWASP Top 10, which was prepared by John Steven, senior director of Security Technology and Applied Research of the Synopsys Software Integrity Group.
According to Steven, Synopsys recommends “replacing proposed entry A7 with a defensible security risk prior to finalizing the new Top 10 list and making it generally available.”
“In general, we caution against including any elements that prescribe security controls or particular security testing in the Top 10 Application Security Risks list, as the newly proposed entries A7 and A10 do. We believe that such inclusions muddle the clarity and purpose of the OWASP Top 10 as well as reduce its utility,” wrote Steven in his article to OWASP.
One of the main issues with the A7 addition is that if the proposed A7 were to be re-worded as risk, it is unclear which we are considering, said Steven. For instance, it could be risk resulting from: Process and other organizational gaps resulting in a security initiative’s lack of patching capabilities; or control-centric gaps resulting in failure of an application to exhibit an emergent behavior coined “attack protection.”
Steven and Synopsys invites other organizations and individuals to consider their position and provide comments regarding the new language to OWASP, by the June 30 deadline. OWASP plans to release the final public release of the OWASP Top 10 2017 in July or August 2017 after the public comment period ends on June 30.