The National Institute of Standards and Technology (NIST) wants to protect users from their mobile devices. The organization has released a new guide designed to improve the security of mobile devices.
While mobile applications have helped businesses increase productivity through real-time communication and connectivity, the benefits don’t outweigh the risks that can come with it, according to the NIST.
“Despite the benefits of mobile apps, however, the use of apps can potentially lead to serious security issues,” the NIST wrote in its report, “Vetting the Security of Mobile Applications.” “This is so because, like traditional enterprise applications, apps may contain software vulnerabilities that are susceptible to attack. Such vulnerabilities may be exploited by an attacker to gain unauthorized access to an organization’s information technology resources or the user’s personal data.”
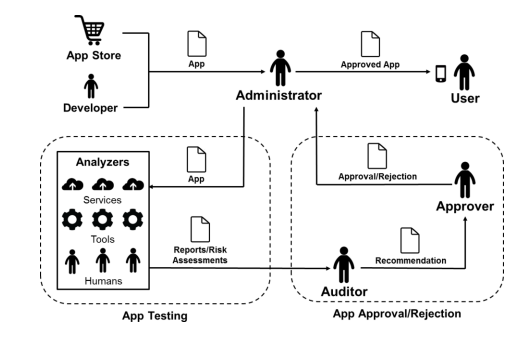
To help protect mobile devices from application vulnerabilities, the NIST said organizations should have an app vetting process that includes app testing and app approval/rejection to determine if the application meets an organization’s security requirements.
“This process is performed on an app after the app has been developed and released for distribution but prior to its deployment on an organization’s mobile device,” the NIST wrote. “An app vetting process acknowledges the concept that someone other than the software vendor is entitled to evaluate the software’s behavior, allowing organizations to evaluate software in the context of their own security policies, planned use, and risk tolerance.”
In order to start a vetting process, organizations must develop security requirements, understand the limits of the process, and set aside a budget and staff to perform the vetting.
The process begins with an administrator or analyzer testing the application, according to the NIST. Not only should the analyzer establish a report detailing any bugs discovered, but he or she should also assess the probability of the bugs being exploited and the impact it would have on a device or network.
“Organizations should not assume that an app has been fully vetted and conforms to their security requirements simply because it is available through an official app store,” the NIST wrote. “Third-party assessments that carry a moniker of ‘approved by’ or ‘certified by’ without providing details of which tests are performed, what the findings were, or how apps are scored or rated, do not provide a reliable indication of software assurance.”
After an application goes through testing, it must then go through an approval or rejection process, according to the NIST. Within this process, an auditor analyzes the bug report and risk assessment and evaluates the criteria to establish whether or not the application violates any of the organization’s security requirements. Based on the auditor’s recommendation, an approver (another high-level member of the organization) determines whether to not an application should be deployed.
“If an app is approved by the approver, the administrator is then permitted to deploy the app on the organization’s mobile devices,” wrote the NIST.
In addition, the report detailed types of software vulnerabilities and testing methods that can be used to detect them.
“Ultimately, the acceptance of an app depends on the organization’s security requirements, which, in turn, depend on the environment in which the app is deployed, the context in which it will be used, and the underlying mobile technologies used to run the app,” wrote the NIST.






