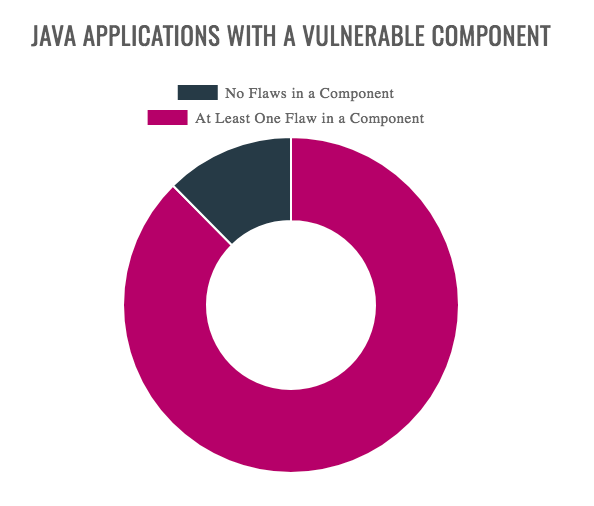
Java developers should be more aware of the open source software components they put in their applications if they want to avoid a security breach. A new report release by Veracode, a CA Technologies company, revealed 88% of Java apps include at least one vulnerable component, and about 53.3% of Java apps rely on a vulnerable version of the Commons Collections components.
“The universal use of components in application development means that when a single vulnerability in a single component is disclosed, that vulnerability now has the potential to impact thousands of applications — making many of them breachable with a single exploit,” said Chris Wysopal, CTO of CA Veracode.
According to the company, the main reason applications become vulnerable is because developers don’t often patch their applications when new vulnerabilities are found or new versions of their components are released. The report, the 2017 State of Software Security Report, found only 28% of organizations conduct composition analysis to track and monitor their application’s components. This becomes a problem when about 75% of application code is made up of open source components.
“Development teams aren’t going to stop using components — nor should they. But when an exploit becomes available, time is of the essence. Open source and third party components aren’t necessarily less secure than code you develop in-house, but keeping an up-to-date inventory of what versions of a component you are using. We’ve now seen quite a few breaches as a result of vulnerable components and unless companies start taking this threat more seriously, and using tools to monitor component usage, I predict the problem will intensify,” said Wysopal.
For instance, when the “Struts-Shock” flaw was disclosed in March of this year, 68% of Java applications using the Apache Struts 2 library were using a vulnerable version of the component, leaving about 35 million sites vulnerable, according to the company.
Other key findings of the report included: 77% of apps have at least one vulnerability on initial scan; governmental organizations have a 24.7% pass rate at latest scan; and critical infrastructure had the strongest OWASP pass rate across all industries.
The report is based off of CA Veracode’s application security testing data from more than 1,400 of its customers.






