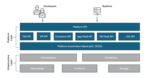
Building end-to-end security into the software development process from the requirements phase through code delivery to production, is easier said than done. Often companies only run a few security tests and activities. That’s no longer good enough. In today’s environment it’s necessary to use multiple techniques to scour the entire software development lifecycle (SDLC) from design, development, deployment, upgrade, or maintenance for security vulnerabilities.
Meera Subbarao, Senior Principal Consultant, Synopsys Software Integrity Group calls this requirement “continuous security” and illustrates it, “We help them with all three aspects of the pipeline; people, process and technology, by providing tools and technologies to use in order to build secure software.” Subbarao, who was with Cigital, prior to Synopsys acquiring the company in October 2016, describes this process as moving to the left. “So, the more tools you give to developers that they can run early when they are writing code, the easier it is for them to find the issues early.”
Several verticals are using Synopsys tools including large financial institutions, all the major cloud providers, and the automotive industry to test and verify their development pipelines.
The tools
Synopsys tools that assist developers while they’re writing code include Secure Assist, that is now going to be integrated with Coverity. Secure Assist is like spell check, it immediately points them to issues and then says, “This is a,” for example, “A sequel injection,” and here is guidance to remedy that.“Going further, the developer may see the issue, but choose to ignore it and check the code into their version control anyway. That is when your continuous integration kicks in, where we have tools like Coverity which you can configure to run as soon as the developer checks in the code, or on a nightly or weekly basis. It’s a static analysis testing tool that scans the code for quality and security issues then notifies the developer and the team.”
Provided there are no issues, the code moves forward to the next phase, building artifacts which is where Synopsys Protecode is a software composition analysis tool. It checks the code for commonly known vulnerabilities and exposures (CVE). It runs through all of the free, open source software you’re using, inspecting it for cyber security vulnerabilities as well as issues like licensing permissions, restrictions, and copy-less licenses. Subbarao notes, “When you use any free or open source tool which has a copy-less license, that it may require the developer to open up the source on the developer’s project. Basically, if you use my open source, then you must open your source. Many companies do not want to open their source code.” Protecode goes through your entire package and your list of dependencies saving heartache and legal actions.
The Seeker is an interactive application security test tool that goes through the entire application to find issues. Load and performance testing tools include a Fuzz test tool and Defensics. Defensics was used to identify the OpenSSL Heartbleed vulnerability that had gone unnoticed for two years and impacted over half a million websites.
Given the latest trend in continuous integration and continuous delivery (CI/CD) and DevOps, code is routinely being pushed to production a few times a day and re-running unnecessary tests slows the process to a crawl. Test Advisor is a new addition to Synopsys’s tool suite. It’s an automated test optimization solution that gives developers the ability to test smarter by prioritizing which tests need to be run due to changes in the code that developers have checked in.
It’s about security
One of the challenges Subbarao sees is that developers and QA don’t recognize and prioritize the security requirements. She reveals, “We actually had a client that was using social security numbers as primary keys in databases. Or another client was using the credit card information, which is really wrong.” Synopsys is helping customers develop and test strong security requirements.
Most of the tools are on-premise although the company is moving toward offering cloud versions. Coverity is one of the tools they have a cloud version of. “Until last year, a lot of the clients wanted everything in-house. Now that the trend is towards cloud, most of the tools need to run in the cloud, so Synopsys is looking to have all of the tools cloud-available in the road map,” says Subbarao. Synopsys differentiates its products based on delivering fewer “false positives” and comprehensive tool use and remediation guidance and support.
Buzzwords
Another concern is the buzzword “DevSecOps” being tossed around. “Just by saying, ‘I have the development team, the operations team and the security team working together,” is not just dev-sec-ops,” points out Subbarao. ‘What the industry needs to acknowledge about dev-sec-ops is that a combination of people, processes, practices must be adopted throughout that delivery pipeline.” This includes continuous integrations, continuous delivery or deployment and then you have to include tools that test end-to-end.
Subbarao emphasizes, “Within Synopsys, we say you need to seamlessly connect all the processes, all the tools, all the DevOps, tool chain, and then eliminate all the bottlenecks, the manual steps, and all the errors.”