The Open Web Application Security Project (OWASP) released its Top 10 2017 project for public comment. This is the 14th year OWASP is raising awareness of security risks with its list, and it contains two major vulnerability updates, example attack scenarios, and a list of free and open resources for security-conscious developers.
When Jeff Williams, OWASP Top 10 project creator and coauthor, first wrote the OWASP Top Ten, he said the application security industry was “shrouded in darkness.” There were only a few individuals who gained knowledge through hand-to-hand combat with applications, and these individuals recognized that they had to make this information public.
“For all the advances we’ve made at OWASP, application security isn’t part of every software project, it’s not taught regularly in university, and it’s often not viewed well by development projects,” said Williams. “In fact, based on the OWASP T10 data we just collected, the average number of serious vulnerabilities per application is a stunning 20.5. That’s an insane number that just shows how far we have to go.”
The OWASP Top 10 2017 release is based on the analysis of over 2.3 million vulnerabilities across 50,000 applications, and it follows the 2013 updates, said Williams. The two major additions to the T10-2017 release includes Insufficient Attack Protection, since one of the most basic security capabilities is being able to detect, prevent, and respond to manual and automated attacks, said Williams. Given the threats applications face, every modern application should have the ability to block these attacks, so they can dramatically improve the ability to defend against both manual and automated attackers, he said.
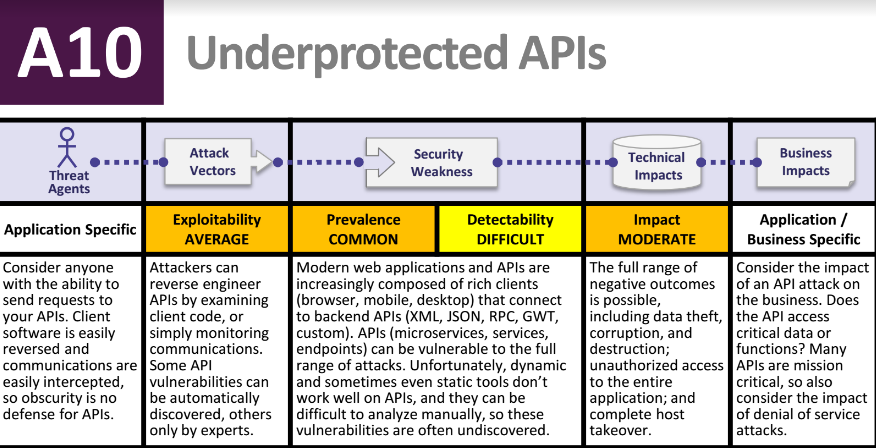
The next major addition is Underprotected APIs, since the use of APIs has exploded in modern software, said Williams. There are a variety of protocols and data formats used by these APIs, including SOAP/XML, REST/JSON, RPC, GWT, and others. It’s important to note that these APIs are often unprotected, and they contain numerous vulnerabilities, said Williams. He also added that these APIs represent a “major blind spot” for security programs in organizations, and OWASP is helping to refocus teams on this expanding problem.
“To me, T10-2017 reflects the move towards modern, high-speed software development that we’ve seen explode across the industry since the last version of the T10 in 2013,” said Williams. “While many of the vulnerabilities remain the same, the addition of APIs and attack protection in this version is designed to focus organizations on the key issues for modern software.”
Williams said it’s important to understand that the Top 10 is an awareness document, but it’s incredibly useful to organizations that have extremely low awareness of application security. He said it can help application security “champions” gain executive sponsorship to start a program, or it could help companies gather information on how they are doing in terms of security.
Application security is optional
According to Williams, companies need to decide if they are going to be an organization that isn’t going to put its business, employees, and users at risk with code that contains known and obvious vulnerabilities. Companies that are not taking application security seriously, or those that choose to ignore the 10 items listed in OWASP’s document are taking a “crazy risk,” he said.
With that in mind, Williams suggests companies review the 10 application security risks listed in OWASP’s Top 10 2017, and he strongly encourages organizations to consider the following:
- Ensure the company has an up to date inventory of what applications and APIs exist.
- Figure out if the business has a threat model and establish a high-level application security architectures with some standard defenses.
- Give development teams (not just coders) the tools and libraries that they need in order to reliably deliver code securely. Be sure they’re trained in application security basics and the details of the company’s program.
- Continuously verify applications for vulnerabilities throughout the software lifecycle, including both known and unknown vulnerabilities. Make sure this includes libraries.
- Check that the company has visibility and control over attacks during operation, so teams can respond in less than a day to any new threat.
- Put in management dashboards to ensure that the company is covering the entire application portfolio, and check that the company achieved the level of security commensurate with the threat model.
Williams said that none of this is “very complicated,” but far more organizations are just getting started with application security. As a result, the application security industry is going to have to reinvent itself, he said.
“Security experts are going to have to figure out how to deliver ‘security as code,’” said Williams. “Essentially, they have to translate every security requirement, every coding guideline, every ‘best practice,’ every threat model, and every security architecture into code that can run during the development, build, test, and deployment process. Even in operations, it’s critical that attack detection and response is fully automated.”
OWASP plans to release the final public release of the OWASP Top 10 – 2017 in July or August 2017 after a public comment period ending June 30, 2017.






