Your teams have taken a lot of time to ensure your super secret systems are super secret, right? Thanks to Black Hat 2015, all that work to prove a system is secure and reliable is going to have to be redone.
Christopher Domas, security researcher at the Battelle Memorial Institute, metaphorically dropped the mic and walked off on what is probably the most interesting exploit I’ve seen come out of the show in years. And remember, this is the year of Stagefright, the “everywhere Android” exploit from JDuck!
(Related: What you’ll need to patch in the next few months)
Domas, it seems, has found what he calls a “Sinkhole” in the x86 APIC. This is an architectural privilege escalation vulnerability. It takes advantage of System Management Mode, which he refers to as “Pandora’s Box.”
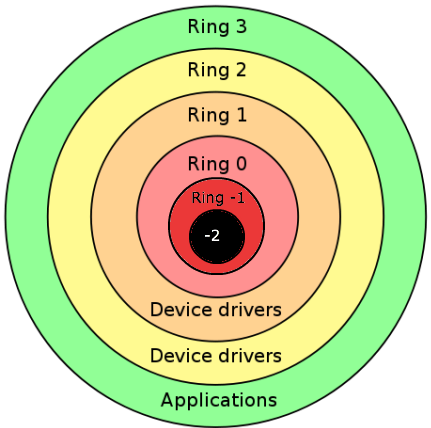
Instead of being happy with hooking into Ring 0 in the processor, Domas described two layers lower than Ring 0, which are hidden from the OS and DMA. The first is Ring -1, the Hypervisor. The second is the Ring -2, where SMM lives.
Using this new ring metaphor, Domas laid out a method of getting through to SMM and issuing it commands. Specifically, he takes advantage of an 18-year-old, forgotten patch to solve a long-dead problem. In 1997, Intel added the ability to relocate the APIC memory registers to another physical address.
Thus the overall strategy for this attack is to find where SMM code is hiding in memory, and to hijack SMM execution privileges. Considering SMM is the trusted based for UEFI secure boot, things could be getting quite messy for your security and data center teams.
What’s the solution? Upgrade to Sandy Bridge and beyond? Use AMD? (Hold off on AMD, as Domas is still checking to see if their chips are vulnerable. The jury is still out.)
Hopefully your production systems are post-Sandy Bridge, which shouldn’t be impossible; the line in the sand is 2012, basically. This could be a good reason to push for that hardware upgrade your team has been asking for.
Should you panic? Of course not. Security threats are generally only as dangerous as those who want to do you harm. If your company has enemies actively attacking it, however, you can bet this vulnerability subset will be poking out to bite you soon enough.
The systems you need to worry about here are those old x86 servers you’ve forgotten about. Does your field office in Nantucket have some super essential server that’s been running silently for 10 years on an old version of Slackware? This vulnerability could, quite literally, be used to burn the office down by turning off thermal controls on the system.
We are through the looking glass here. This is some Gibson-level potential. With control of SMM, attackers can fiddle with hardware-level crypto, power management, system controls, firmware, and just about anything else you can think of that’s physically attached to a machine.
These things have not happened yet, and the level of expertise needed to exploit this bug to do these things is certainly high. And, to top it off, you do need access to Ring 0 memory to get to SMM, so using this for privilege escalation is questionable right now. I figure Domas has a solution to that, though: He’s dropping more code to exploit this over time.
Isn’t Black Hat fun?






