GrammaTech has announced a new software composition analysis (SCA) product, CodeSentry, that is designed to detect vulnerabilities in application components including binaries, and create a detailed software bill of materials.
According to the company, it identifies blind spots and allows security professionals to measure and manage risk quickly throughout the SDLC.
With the bill of materials, CodeSentry can detect the components and vulnerabilities associated with them, including network components, GUI components, or authentication layers.
“Using third party components rather than building applications from scratch is an accepted practice for accelerating time to market and is fueling a massive growth in reusable code,” said Mike Dager, the CEO of GrammaTech. “Most organizations now recognize the security risks that third-party code poses to their applications and business, and the need for software composition analysis provided by CodeSentry, which inspects binaries for unmatched precision.”
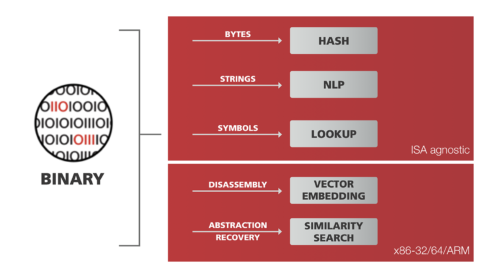
The solution is based on GrammaTech’s binary code analysis and machine learning technology that delivers deep visibility without the need for source code by providing an application upload interface that accepts native binaries, zip files or other archives.
It also analyzes the code that will run, not the build environment, which significantly reduces false positives due to superfluous code in build environments as well as components that are excluded due to build configurations, according to GrammaTech.
In addition, CodeSentry identifies components present in native binaries through a variety of component matching algorithms to gather version number ranges, create a SBOM and provide links to CVE and CVSS scores.
“Customers using first generation software composition analysis tools that rely on source code to identify third party components are often at a disadvantage as they do not have visibility into software that is delivered as binaries,” said Vince Arneja, the chief product officer for GrammaTech. “GrammaTech’s ability to provide binary analysis and create a software bill of materials eliminates this dangerous blind spot so organizations can proactively shrink their attack surface.”






