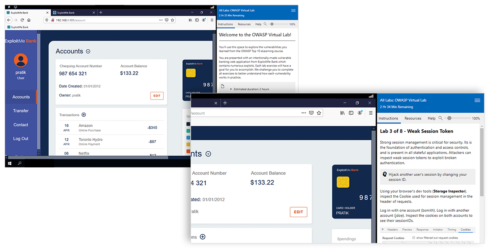
Security Compass has announced a hands-on training lab for balanced development automation. The new interactive virtual lab offers training across multiple exploit scenarios to help developers understand common vulnerabilities and how to build secure software, the company explained.
The training lab can now be added to existing subscriptions for the Software Security Practitioner (SSP) Suites, a role-based e-learning program, or Full Library, which has 35 on-demand courses for required education or personal interest.
“Professionals are increasingly seeking innovative ways to learn new skills, and test this knowledge in a safe environment,” said Lauren Park, the director of training at Security Compass. “We are committed to providing new ways for developers to gain this knowledge, and are proud to launch our hands-on training lab as the latest resource for customers to improve their security posture.”
Capacitor Core plugin changes
As of Capacitor 3.0 beta, all officially supported plugins are now installed and versioned separately from Capacitor core, which gives developers more control over what APIs are included in an app.
Ionic, the company behind the cross-platform app runtime said that the migration is “fairly straightforward” in a blog post. Developers who have customized their native projects should manually update them to accommodate these changes in Capacitor.
Ionic added that it is currently working with the Capacitor Community GitHub Org to help update the third-party plugins to the new API.
Apache weekly updates
Last week at Apache saw the release of Apache Tika 2.0.0-ALPHA, which includes a major refactoring of the modules to enable more fine-grained selection of resources and more.
Other new releases included Qpid Broker J 7.1.11 and J 8.0.3, CloudStack v4.15, Jackrabbit Oak 1.22.6, and Camel 3.7.1.
Apache Superset, the open source data exploration and visualization platform, reached Top-Level Project status, moving one step closer to graduation status.
Apache also found two vulnerabilities: Guacamole CVE-2020-11997, which has an Inconsistent restriction of connection history visibility and Tomcat CVE-2020-17527, which involves a Apache Tomcat HTTP/2 Request header mix-up.
Additional details on all of the updates are available here.