Malicious hackers will find any way to deliver a cyberattack. This week, Check Point Software researchers discovered a new method for perpetrators, one which is threatening millions of users: Attacking by subtitles.
According to Check Point’s research, the new possible attack vector delivers the cyberattack through movie subtitles that are loaded by the user’s media player.
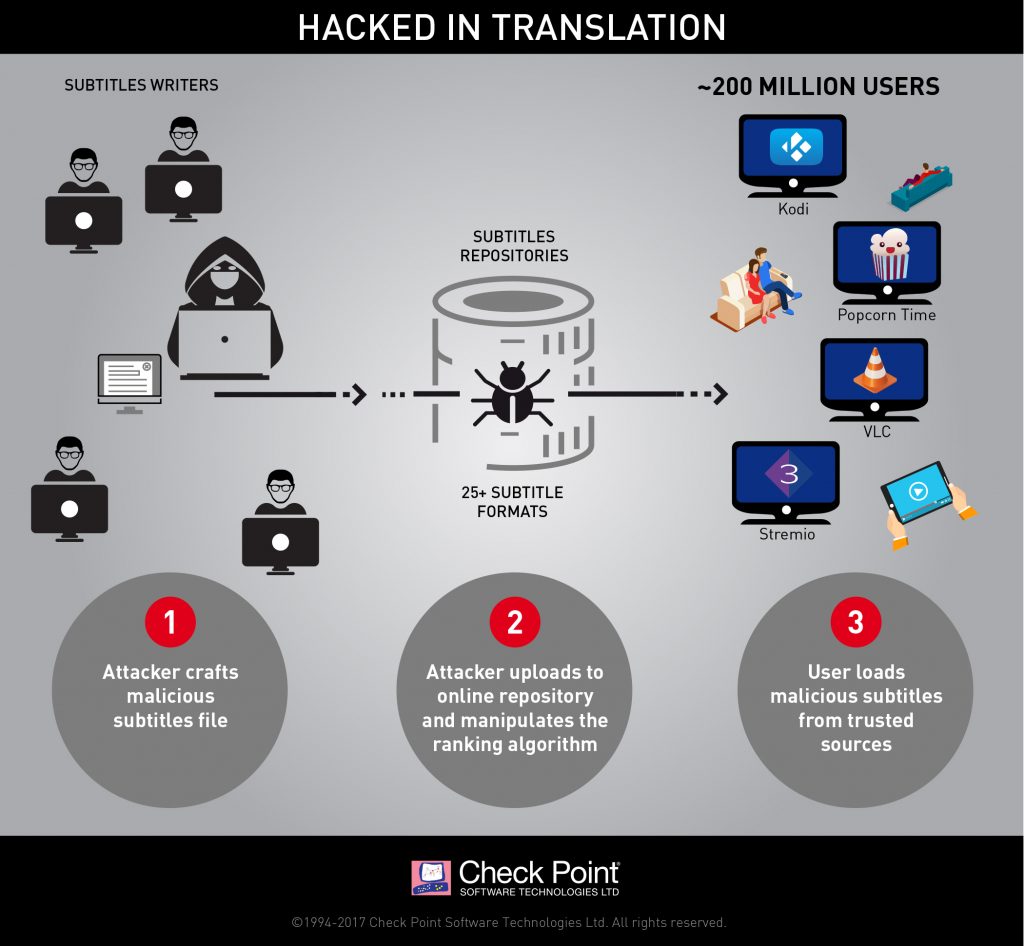
The researchers found the subtitle repositories can be manipulated and “made to award the attackers malicious subtitles a high score, which results in those specific subtitles being served to the user.”
This method is particularly dangerous because it requires no action of the user, and anti-virus software and other security solutions may vet the attacks without trying to “assess their real nature, leaving millions of users exposed to this risk,” said the team.
The real root cause of the attack vector is due to the poor state of security in the way media players process the subtitles and subtitle formats. According to Check Point, there are more than 25 subtitle formats in use, and media players need to parse together multiple formats, with each media player using a different method.
The number of affected users is in the hundreds of millions, says Check Point, and once the hacker gets in through the subtitles, the researchers say they can do whatever with the victim’s machines, whether that be PC, a smart TV or a mobile device.
“Anyone who uses an old version of VLC media player or Kodi media player is at risk for this attack,” said Alex Heid, chief research officer at SecurityScorecard. “Hackers can craft malicious subtitle files that will execute arbitrary code within the media player, exposing the user to potential malware activity. The media players are not expecting executable code, and ‘tricked’ into running the code thinking it is an innocent subtitle track.”
Check Point found vulnerabilities in four prominent media players: VLC, Kodi, Popcorn Time and Stremio. Some issues were already fixed but at this time, Check Point is giving developers time to address the vulnerabilities before they publish any further details. Users can start by updating their platforms immediately, especially if using VLC or Kodi, said Heid.
“Once updated, this attack vector will be closed,” said Heid. “This attack can spread through video files on P2P networks, or from files served up on malicious websites.”