Black Duck, a company that serves up information about the latest security vulnerabilities on open source components, released its 2017 Open Source Security and Risk Analysis (OSSRA) today. The OSSRA revealed significant risks related to open-source vulnerabilities and license-compliance challenges, as well as high levels of risk in the retail and ecommerce industry.
According to Mike Pittenger, Black Duck vice president of security strategy, Black Duck conducts open-source code audits annually, primarily related to Merger & Acquisition transactions. In 2016, the organization analyzed 1,071 of the applications audited during that year and found both high levels of open source usage and significant risk to security vulnerabilities in the apps it measured.
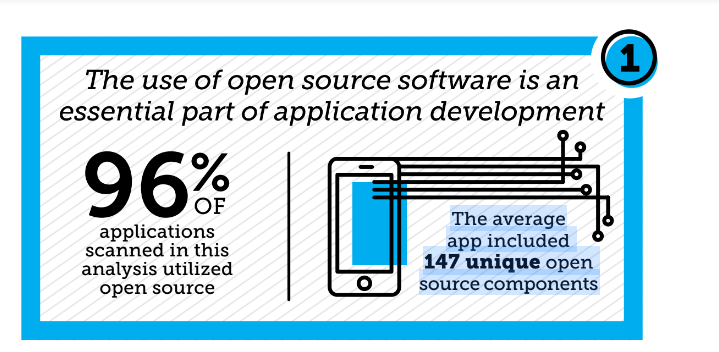
The audit of applications found 96% of the apps contained open source, which was no surprise, but what was shocking was more than 60% of the apps contained open-source vulnerabilities, said Pittenger. Black Duck also found that two-thirds of the applications the company looked at had vulnerabilities in the open source, and about 27 vulnerabilities were in the application at large.
There was also a big jump in the number of unique components in the average application, which went up to 147 components this year, compared to last year’s 105 open-source components, according to Pittenger. Another interesting find came from asking the code owners if they have a list of the components they use, and according to Pittenger, the vast majority do not. For the minority of code owners that do have a list of components, Black Duck found that they only know of about 45% of the components they are using. Most code owners think that they are using about 60 to 70 components, when really they are using close to 150 in the application, said Pittenger.
According to Pittenger, Black Duck also measures the age of vulnerabilities by looking at the date of when the vulnerability was publicly disclosed, and the date of the audit. The average age of vulnerabilities was over four years, said Pittenger.
Often times, these components are being directly added to the codebase with the vulnerabilities present. And the other fact is, developers and companies may not be tracking these components, and if they don’t have visibility, then they can’t do anything about it if the vulnerability is disclosed, said Pittenger.
“We don’t take the position that open source is any less secure than commercial software, nor is it more secure, frankly, because it’s software so it’s going to have bugs and vulnerabilities,” said Pittenger. “There are some characteristics about open source software that make it attractive to an attacker, simply [because] it’s ubiquitous and it’s a target-rich environment.”
Additionally, Pittenger highlighted unknown licenses as additional risks that industries need to consider. Black Duck saw unknown licenses in over half the applications, and found that companies were out of compliance in over 85% of the code bases. This means companies could be using code incorrectly, or they could be putting their IP addresses at risk, he said.






