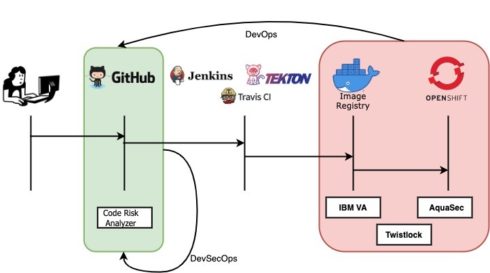
IBM has announced the Code Risk Analyzer, a focused effort to bring security and compliance analytics to DevSecOps.
The Code Risk Analyzer can be configured to run at the beginning of a developer’s code pipeline and it reviews and analyzes Git repositories for known issues with any open-source code that needs to be managed. It helps provision toolchains, automates builds and tests, and enables users to control quality with analytics, according to the company.
“The trend toward decentralized cloud-native developer teams creating, modifying, and redeploying their work on a daily, or more frequent basis, has sparked a transformation in security and compliance processes for business applications,” Shripad Nadgowda, senior software engineer at IBM, wrote in a blog post. “As a result, it has become critical to equip developers with a new set of cloud-native capabilities and tools, such. Code Risk Analyzer, that can be easily embedded into existing development workflows.”
While previous solutions focused on running at the beginning of a developer’s code pipeline, the solutions were found to be inefficient because container images have slimmed down to where they contain the minimum payload needed to run an application and images lack the development context of an application.
“In DevSecOps it’s absolutely essential to design a comprehensive and consistent solution that encompasses security and compliance assessment across all these artifacts. As a result, we embodied them all in the scope for the Code Risk Analyzer solution,” Nadgowda wrote.
For application artifacts, Code Risk Analyzer aims to provide vulnerability, license management, and CIS checks on deployment configurations, generates a Bill-of-Materials and security lint checks. Terraform files (*.tf) used to provision or configure cloud services like Cloud Object Store and LogDNA are also scanned to identify any security misconfigurations.
The solution also provides a separation of concerns between developers and security experts through a role-based Open Policy Agent (OPA) framework for controlling such policies. The analyzer is also embedded into developer workflows and includes a change request procedure through pr_workflow for a pull request, and a change request approval by commit-to-main-branch in ci_workflow for continuous integration.
The addition of Smart Updates, tracks changes to all dependencies of an application and classifies those changes through automated update notifications.
Additional details on IBM’s Code Risk Analyzer are available here.






