The Open Web Application Security Project (OWASP) officially released its Top 10 most critical web application security risks. This is the first time the organization has updated the Top 10 since 2013.
“Change has accelerated over the last four years, and the OWASP Top 10 needed to change. We’ve completely refactored the OWASP Top 10, revamped the methodology, utilized a new data call process, worked with the community, re-ordered our risks, rewritten each risk from the ground up, and added references to frameworks and languages that are now commonly used,” the OWASP wrote in the Top 10 2017.
According to the OWASP, some significant changes over the past couple of years that resulted in an update to the Top 10 include microservices, single page apps, and the dominance of JavaScript as a primary language on the web.
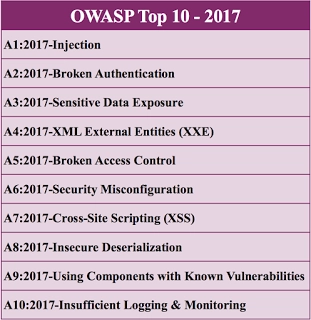
The Top 10 now consists of:
- Injection
- Broker Authentication
- Sensitive Data Exposure
- XML External Entities (XXE)
- Broken Access Control
- Security Misconfiguration
- Cross-Site Script (XSS)
- Insecure Deserialization
- Using Components with Known Vulnerabilities
- Insufficient Logging and Monitoring
XXE, insecure deserialization and insufficient logging and monitoring are new to the Top 10. Broken access control is a combination of 2013’s insecure direct object references and missing function level access control. In addition, the OWASP has removed unvalidated redirects and forwards, and cross-site request forgery from the Top 10.
“Why have CSRF and unvalidated redirects and forwards been removed? It’s time to move on. The data for these is no longer strong enough to warrant inclusion, especially when we only have 8 data supported spots with our new methodology, and these two items didn’t rank in the community survey. This is actually a sign of success; the fact that CSRF is finally going away is a sign that the OWASP Top 10 has been successful at its mission,” the OWASP wrote in a blog post.
The community survey, which received more than 500 responses, did agree on the inclusion insecure deserialization and insufficient logging and monitoring, according to the OWASP. “These two items were obviously top of mind for many this year considering the era of the mega breach is not slowing down,” the OWASP wrote.
According to the OWASP, insecure deserialization leads to remote code execution, and insufficient logging and monitoring coupled with missing or weak integration results in hackers being able to attack systems and maintain persistence.
XXE is a new category supported by data. “Many older or poorly configured XML processors evaluate external entity references within XML documents. External entities can be used to disclose internal files using the file URI handler, internal file shares, internal port scanning, remote code execution, and denial of service attacks,” the OWASP wrote.
To defend against the Top 10, the OWASP believes developers need to establish and use repeatable processes and security controls, security testers need to establish continuous application security testing, application managers need to take charge of the full application lifecycle from an IT perspective, and the organization as a whole needs to have an application security program in place.
“A great deal of feedback was received during the creation of the OWASP Top 10 – 2017, more than for any other equivalent OWASP effort. This shows how much passion the community has for the OWASP Top 10, and thus how critical it is for OWASP to get the Top 10 right for the majority of use cases,” the OWASP wrote.






