Cybersecurity costs companies billions of dollars a year, with that cost expected to be in trillions by 2025, according to some cybersecurity research firms. Consider the Marriott hotels’ leak of 500 million customer records for which Marriott took a $126 million charge; and Equifax, an American credit reporting agency, spent 1.4 billion dollars on cleanup costs associated with the 2017 data breach of 150 million personal credit histories.
The average cost of a data breach in 2020 is $3.92 million. Beyond monetary implications, a large security incident has the potential to decimate a company’s brand and even be a career-ending event for the top executives.
The past few years have taught us that every layer of the stack – from hardware all the way to JavaScript in a web browser – can have security vulnerabilities. In the meantime, security has evolved to be a collective responsibility of everyone building and running IT systems, including developers, as enterprise IT leaders recognize that security must be integrated and continuous in today’s cloud native environments.
In “Securing Cloud Applications on Kubernetes,” we understand that computer security is a vast field with many different technologies that must be learned independently, then combined correctly in an application. Application developers and architects typically learn security technologies on the job when they first encounter them while under pressure to deliver product features and bug fixes. Reading blog posts, cutting and pasting configuration settings, and searching stackoverflow.com for help while under pressure to deliver leaves developers feeling like they don’t understand security but also don’t have the time and resources to properly learn it.
Making sense of application security
Application security is in the midst of its own transformation. It’s not only recognized as a necessary discipline, it’s also become part of the daily work of multiple teams, including app developers. The heightened focus on security by senior business leaders affects application developers in multiple ways:
- Use all product security features: CISOs expect developers to use every security feature available in products to secure an application. Do you know how to configure and use the security features in the application server, database, object store, message broker, API gateway, service mesh, cloud services, programming language and development frameworks being used on a project you are working on? It is no longer enough to know how to use a product, you must know how to use it securely.
- Follow corporate security standards: CISOs expect applications to pass strict corporate security assessments and audits. As a developer you must be able to explain to assessors and auditors how your application meets corporate security standards. This means you need to be able to speak the security language used by information security professionals so you can avoid costly remediation work to fix security issues late in the development cycle.
- Design and implement secure applications: CISOs expect architects and developers to design and implement secure applications. This means that you must be familiar with many security protocols and technologies required to design and implement secure applications.
- Enable DevSecOps Transformation: CISOs are investing heavily in breaking down the silos between the development, operations, and security teams. This means that as a developer you need to become familiar with new tools, processes, and practices used to implement DevSecOps.
The diagram below provides a map of the broad areas of application security.
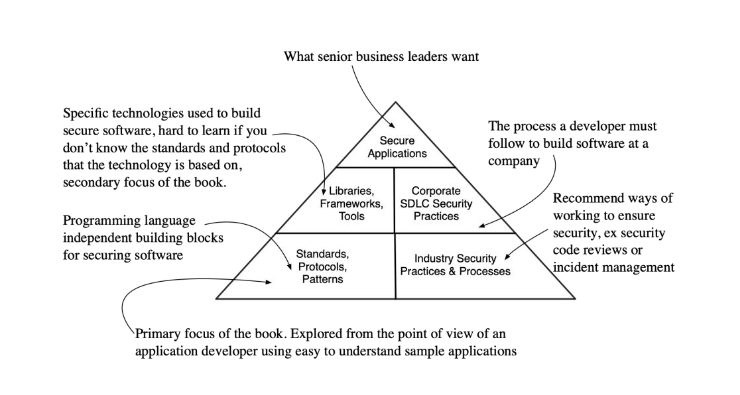
The top of the diagram above represents the goals of senior business leaders to build secure applications that can stand up to attacks. The higher layers of the diagram depend on the layers below them. To secure an application you need to use security libraries, for example a Java web application might use Spring Security to authorize user access. Security libraries are not enough to provide security, though. You must design, code and maintain the application in a secure way by following the corporate security practices for application development, for example performing a security code review, or setting code analyzers that detect common security coding mistakes. As a developer you spend your time in the middle layer of the pyramid above.
Security libraries and frameworks implement industry standard protocols and patterns in a specific programming language.
The root cause of developer difficulties using security libraires is lack of knowledge about the underlying standards, protocols and patterns the libraries implement. If you understand the underlying security standards, protocols, and best practices you will find security libraries and frameworks much easier to use and learn.
The first step in the learning journey is to build a big-picture mental model of application security use cases and the available approaches for solving them. We start the learning journey by analyzing two common security problems:
- Securing communication channel
- Securing application dependencies
Examining how to secure communication channels and application dependencies enables us to make sense of types of skills an application developer needs to know about security and map out an effective approach for learning security skills.
Analyze a common set of security problems encountered when building monolithic and microservice based applications so that you can have a big-picture understanding of the security technologies and standards that every developer should be familiar with in order to build secure cloud native applications.
Securing communication channels
It is tempting to assume that there is no need to encrypt communications between the application backend and its database because the traffic is on a “trusted” internal network.
It is a best practice to operate under the zero-trust networking model where you assume that the network is always untrusted. Treat the internal data center network with the same level of suspicion that you treat the internet. As an application developer it is important that you insist on Transport Layer Security (TLS) everywhere for any application network communications. Getting comfortable with the TLS protocol is a critical security skill for developers. Mastering TLS enables you to:
- Write secure applications that meet corporate security standards.
- Quickly configure TLS in your code without spending hours searching blogs and stackoverflow.com for setup instructions.
- Debug connectivity issues caused by TLS configuration settings easily.
There is a tangled web of algorithms based on deep beautiful mathematics at the heart of TLS. You do not need to understand how these algorithms work or the math behind them, but you must understand what they do and how to configure them correctly in your applications.
Securing application dependencies
Applications are built on top of hundreds of open-source libraries and proprietary software components. For example, at time of writing I am working on a Spring Boot application that depends on 106 open-source third-party libraries. I have seen some enterprise applications with 250+ library dependencies. Reusing software components across applications is a huge time and cost saver, however it also introduces the possibility for catastrophic security failures.
Supply chain security is an industry wide problem since every software producer depends on external code suppliers who in turn depend on other suppliers, etc. New security tools and processes must be built then adopted widely to secure the software supply chain.
Continuous automated dependency vulnerability detection
You can easily detect vulnerable dependencies using an automated vulnerability scanner. The vulnerability scanner builds a list of all the dependencies an application uses by analyzing the application’s code, build scripts and generated artifacts. The scanner compares the application’s dependency versions against a database of known vulnerabilities. If a match is found the scanner alerts the development team.
Computer security is a massive topic with many different subfields and specializations. It can take a lifetime to master computer security. As a developer you must focus on the subset of computer security that is most relevant to your needs for writing secure applications.
Summary
- Never trust the network: Treat internal “secure” networks with the same level of trust as the internet. Secure all application communication channels using TLS protocol.
- TLS is a key foundational technology that every developer should know really well.
- Software supply chain attacks are increasing because they are extremely effective. Use a dependency vulnerability scanner in all your applications, rapidly fix issues flagged by the vulnerability scanners. Stay up to date with advances in software supply chain security tools and processes and champion their use with your employer.
- The goal of DevSecOps is to reduce the time, effort, and cost of taking a business idea from concept to production while applying the best practices of security, operations and development.
- Security is the collective responsibility of everyone working in IT including developers. Improving your security skills makes you more valuable to your employer and enables you to resolve security issues quickly.
(Excerpt from the pre-publication book “Securing Cloud Applications on Kubernetes” by Adib Saikali)
To learn more about the transformative nature of cloud native applications and open source software, join us at KubeCon + CloudNativeCon Europe 2023, hosted by the Cloud Native Computing Foundation, which takes place from April 18-21.






