Open-source libraries reliant on serverless architecture frequently skimp on essential security measures, according to serverless security runtime environment provider PureSec’s Ten Most Critical Security Risks in Serverless Architectures 2018 report.
The analysis found critical vulnerabilities or misconfigurations that “could allow attackers to manipulate the application and perform various malicious actions” in 21 percent of 1,000 open-source libraries. Ory Segal, chief technology officerand co-founder of PureSec, said he and the other surveyors didn’t expect some of the types of vulnerabilities they observed.
The most critical issues PureSec outlines in the survey, in order of decreasing severity, are:
- Function event data injection
- Broken authentication
- Insecure serverless deployment configuration
- Over-privileged function permissions and roles
- Inadequate function monitoring and logging
- Insecure third-party dependencies
- Insecure application secrets storage
- Denial of service and financial resource exhaustion
- Serverless function execution flow manipulation
- Improper exception handling and verbose error messages
“Personally, I was surprised by the fact that application security still seems like an afterthought when it comes to serverless architectures,” Segal said. “It’s as if everything we’ve learned about application security in the past 20 years didn’t quite stick, or perhaps folks didn’t think it was relevant in the case of serverless.”
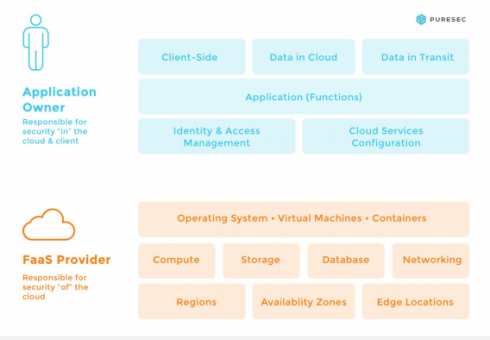
While serverless relies heavily on micro and nano-services, with much of security and physical infrastructure falling under the purview of a cloud provider, there are still a multitude of critical areas that are still the sole responsibility of the application owner.
“Serverless makes the lives of developers a lot easier – you can whip up rich full-blown applications within in hours, and you don’t have to rely on an IT team to deploy or maintain it.,” Segal said. “It’s an enabler for fast, rapid software development. However, like any other software, you have to build it in a secure fashion – by the book. There are no shortcuts to application security.”
But serverless architecture is a relatively new option, and Segal says the documentation that might set people on the right path simply isn’t there.
“Up until the release of the The Ten Most Critical Security Risks in Serverless Architectures 2018 guide, I haven’t seen a single comprehensive and all-encompassing attempt to document the most critical issues that require attention from developers and software architects. There were a lot of bits and pieces, blogs, scattered around the Internet, but the material wasn’t well organized in a way that would help developers to get educated properly before starting to build serverless applications.
Most of what Segal and his team came across in their trawls were focused on granular, serverless-specific security topics with little attention paid to the more base-level application security where PureSec’s survey found vulnerabilities.
“My guess is that when it comes to a new technology, people tend to gravitate towards the new and unknown,” Segal said. “There was a lot of attention around roles and permissions, at least in the AWS Lambda case. While this is indeed a critical topic, it’s definitely not the top most critical issue.”
Though Segal says the full report is great information for anyone in need of security guidance for their serverless architecture, “if you only have 10 minutes to spend – I would say, pay close attention to the ‘Serverless Security Overview’, which is actually the introduction to the paper. It describes the paradigm shift that is required in application security.”
As far as ways to start alleviating the significant security shortfalls PureSec found, Segal says people can’t forget about security requirements and threat modeling while enjoying the ease-of-use and rapid deployment of serverless solutions.
“Keep in mind that serverless is just an architecture used for developing applications,” Segal said. “Re-use everything you’ve learned about how to secure applications. Never trust or make assumptions about the validity of inputs (which are much more diverse in serverless architectures), harden your cloud environment, and make sure you harness the right tools and technologies to help you protect your serverless applications. Most of the traditional application security solutions won’t be suitable as you can’t deploy them, so make sure you evaluate each solution and make sure it’s relevant for your environment.”






