The triple effect of cloud adoption, DevOps and CI/CD has dealt a blow to the old tried-and-tested means of infrastructure provisioning and configuration. Thanks to the increasing size of software, its dependencies and support of various platforms, these predominantly manual and script-based tasks have been getting increasingly cumbersome, time-consuming and error-prone.
This is where Infrastructure as code (IAC) and Configuration as code (CAC) come to the rescue. They enable the automation of many aspects of infrastructure provisioning, maintenance and software configuration tasks.
Infrastructure as Code has enabled on-demand deployment of configured infrastructure tailored specifically for the applications that it is designed to run. Earlier, infrastructure was provisioned manually through one-off configuration scripts which were run by operations engineers. This was often error prone, slow and brittle. Through Infrastructure as Code, operations environments are managed programmatically with the same rigor that is mandated for any code-based development. This has enabled version control and also ensured repeatability of environment provisioning.
As familiarity and confidence in IAC and CAC grows, organizations increasingly understand the advantages in terms of speed, standardization and flexibility when supporting a CI/CD pipeline.
But, where to start?
Choosing the right set of tools
One size does not fit all so there may not be one tool or tool-combination that works for all types of applications and environments. This is particularly true of infrastructure and configuration as code. However, there are tested and proven combinations of tools that are recommended for certain types of applications, technology stacks, deployment environments and use cases. This article takes a look at a couple of these in more depth later. But first, here are some of the factors that play an important role in tool selection.
- On premise vs. cloud
Cloud offers high availability and auto-scaling benefits, while on premise is a comparatively cheap option. A hybrid approach should also be considered, keeping some critical components in the cloud.
- Security
Ensure the management of roles and permissions meets the needs of the organization.
- Technology
Be aware of vendor lock-in. Select tools that offer support for a number of technologies, so that future projects can also benefit.
- Open source vs. proprietary
Weigh the benefits of any paid and proprietary tools against their open-source counterparts. When considering open source, look for community support and activity.
- New entrants
Regularly review the new entrants and trending tools on the market. They are often innovators who have actively addressed the weaknesses of industry-leading tools.
- Feedback
Creating working feedback loops is especially important for CI/CD. Check that tools support feedback notifications for multiple channels, e.g. email, instant messaging and support for team collaboration tools like Slack or HipChat.
- Analytics
Usage data and other important analytics metrics provide key data to help make informed business decisions. Know what each tool offers and how it aids the team’s data analytics.
- Maturity
The last thing an organization needs is to experience teething problems from immature tools that were not properly tested. Check industry feedback and recommendations carefully.
- Community support
Whether it is a paid-for technology or open source, be sure of the level of support you’ll be getting. Inadequate support can lead to delays that block the entire deployment pipeline – a situation that can be avoided through either paid support services or with the help of a dynamic support community.
Tool Selector: Ready to take the plunge?
There are so many different methods used for software deployment, testing and delivery. And for each type of infrastructure – cloud or on premise or hybrid – there are many tools and technologies available to choose from. Based on our research, here are the leading ones in each category:
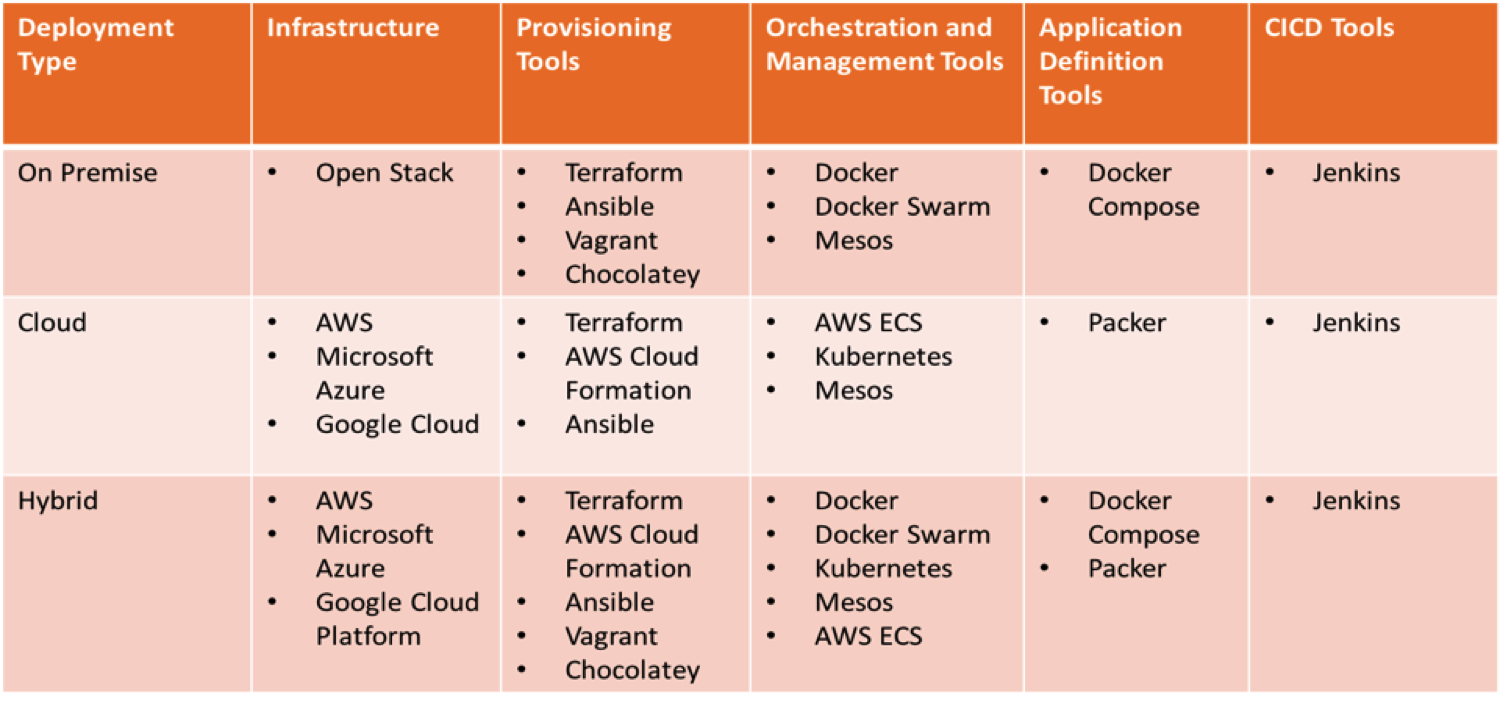
Getting off to a strong start with tool combinations
Here are two proven tool combinations to smooth the transition and speed up delivery.
- Vagrant + Docker + Ansible
This combination allows developers to package the development environment and push it across the organization or team.
Pros:
- One-shot installation of pre-configured software and tools
- OS-level abstraction – Vagrant
- Easy software installation – Docker
- Easy software maintenance – Ansible
Cons:
- Overhead of running Vagrant VM
- Learning curve for developers to understand and use Vagrant and Docker
- Lack of Mac OS support e.g. cannot run XCode in this environment
Ideal Use Case:
Imagine the scene: a new project has kicked off and the development team needs to be on board with systems involving JDK 8, My SQL, IDE and Apache Tomcat. Instead of every developer preparing for the development environment, and all the inefficiencies that this approach represents, this combination allows the team to provide a consistent development environment and save many hours.
- Terraform + AWS + Jenkins
This tool combination is ideal for deploying staging and production environment software.
Pros:
- Easily create, update, scale or tear-down services
- Supports multiple providers in parallel (e.g. AWS, Azure, Google Compute Cloud, Digital Ocean, Heroku)
- Abstracts APIs of individual providers thereby making it simpler to manage services
- Easily switch from one provider to another based on technical, business or other decisions
- Easier CI and CD with Jenkins orchestrating the execution of tasks
- Works with most development technologies irrespective of packaging (e.g. Docker, non-Docker, serverless)
Cons:
- Terraform is a CLI tool. Hence it may not be possible to create a GUI-based only tool/ platform that can work in the cloud / browser without a normal system on the back end.
- Learning curve for understanding and using Terraform for the team. The learning and testing period may incur costs as the output of one action may be the input of another and practical testing will result in live operations.
- AWS services must be optimally utilized to manage costs. This may require a significant learning curve or expert consultancy
Ideal Use Case:
A team has developed an application that has a number of software dependencies with specific configurations; the staging and production environment are maintained on AWS. Here, we can use Terraform to create any new instances, services and configure them without touching the AWS GUI or referring to AWS API or CLI commands. The existing services can be scaled or destroyed and any output values that need to be passed as input to another service can be fully automated.
Other mashups are possible, of course. We have seen combinations like these work for large banking/financial and healthcare services companies.






