As a way to help developers prevent disclosure of sensitive information or help them identify potentially dangerous commits, SourceClear has open-sourced Commit Watcher, a tool that finds both accidental credential leaks and security patches before they become an issue.
Commit Watcher finds interesting or potentially hazardous commits in Git projects, according to its GitHub page. It allows developers to check up on their own projects to make sure they didn’t leak AWS keys or other credentials, and they can also check other open-source projects for potential security vulnerabilities and patches.
(Related: Open-source blueprint Pepperoni released for mobile development)
The tool works by looking for keywords and phrases in code commits and commit messages that are often associated with an undisclosed security patch, according to Brian Doll, vice president of marketing and community at SourceClear. He gave an example of when a commit message includes the phrase “fixes XSS attack,” which likely means that a project was previously vulnerable to a cross-site scripting attack.
When setting up Commit Watcher, developers can run it locally, which is good for fast development, or they can run it with Docker. The process starts every few minutes when a project hasn’t been checked in a while and it’s polled for new commits. These commits are checked against whatever rules are setup for the project, according to the GitHub page.
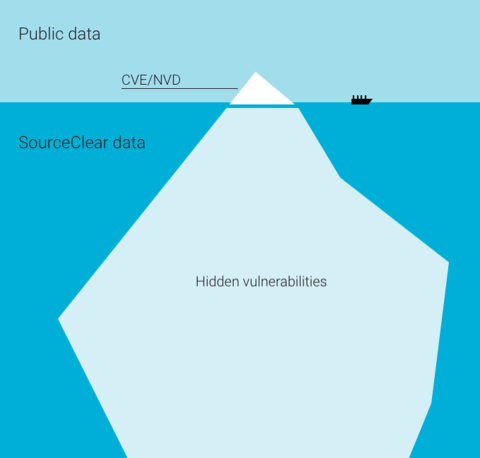
Developers who want to use open-source software safely can use Commit Watcher to check if there are any leaked credentials or security issues without waiting for the Common Vulnerabilities and Exposures (CVE) system.
Doll said that the intended goal of the CVE is to manage canonical names for disclosed vulnerabilities. There are a few ways someone can begin to request a CVE, which is part of the problem.
“Most open-source projects don’t have a dedicated security team, and don’t have experience managing the CVE process,” said Doll. “Instead, they’re focused on fixing vulnerabilities in a timely manner, which is incredibly important. Unfortunately, if you are using a vulnerable version of that project, you won’t know how important it is to upgrade without some form of disclosure.”
Since the CVE process isn’t widely used across the open-source community, developers can use tools like Commit Watcher, which informs them of open-source vulnerabilities without waiting. Also, developers can use the SourceClear Registry, which is a database of open-source vulnerabilities. Doll said that it augments public vulnerability data sources with vulnerabilities that its security research team discovers.
Commit Watcher is already preloaded with dozens of rules to find commits containing credentials from AWS, Salesforce, SSH keys, API tokens and database dump files, according to the company. The developer community can also get involved and contribute any undisclosed security patches or rules that they find to be useful.






