Wind River unveiled its latest offering, the Wind River Studio Linux Security Scanning Service. This service, designed specifically for embedded Linux development, offers high-quality scanning capabilities to detect and identify Common Vulnerabilities and Exposures (CVEs) and is currently accessible to users free of charge.
The new service goes beyond detection and also provides information on the availability of remediation solutions for each CVE, including relevant fixes and patches offered by Wind River.
With this new service, Wind River aims to support organizations in enhancing the security of their Linux-based systems while catering to the unique requirements of embedded Linux development.
“In a highly connected and complex computing landscape where security exploitations are becoming more prevalent, the effective and proactive monitoring and management of CVEs is a top priority. In the rush to add new features, get to market faster, and achieve platform stability, CVEs often go inadequately addressed in the maintenance lifecycle,” said Amit Ronen, chief customer officer of Wind River. “Leveraging our many years of Linux experience and expertise, Studio Linux Security Scanning Service helps developers quickly identify high-risk vulnerabilities, prioritize remediation efforts, and enhance the security of their Linux-based devices and systems.”
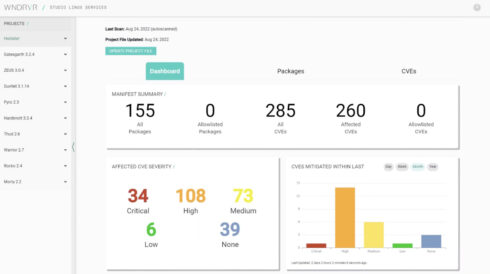
The Wind River Studio Linux Security Scanning Service operates by analyzing SBOMs or manifests provided by developers. It examines various layers of the platform, such as the kernel, user space, libraries, and system components. By comparing this information against a comprehensive knowledge base, the scanner accurately identifies critical vulnerabilities.
Additionally, the scanner can display the licenses used in the platform’s packages, aiding in artifact generation and compliance requirements. The identified vulnerabilities are then ranked based on the Common Vulnerability Scoring System (CVSS v3). The service relies on a knowledge base built from a curated collection of data sources, including the Yocto Project, NIST, and Wind River’s own CVE database.






