Jeff Williams, co-founder and CTO, Contrast Security:
Contrast is an integration platform for application security. We use an instrumentation-based approach, so we work from inside the running application layer. From there, we support the entire software life cycle with three things. The first thing is, we help identify vulnerabilities. Typically you want them to be discovered really early in the life cycle, so that’s what we do. As developers are writing their code, they can get instant feedback on the code that they’re writing, they can fix those problems the way they normally could, and they can check in clean code without breaking stride. There is no scanning.
RELATED CONTENT: For effective DevSecOps, sift left AND extend right
I want you to imagine all of your applications — there could be thousands of applications in an enterprise — I want you to imagine them all testing themselves simultaneously, as opposed to having to go to each one and scan it, serially. It’s a very scalable approach to application security, finding vulnerabilities.
The second thing that we do is we analyze open-source libraries for both known and unknown vulnerabilities. So this is really a big deal. There have been a bunch of big breaches related to the use of open-source libraries. Contrast is an effective way of doing that at scale in real-time across the organization, and our big differentiator there is that we can tell you exactly how each of those libraries is being used. Instead of just saying, ‘you’re using that library, therefore you have to replace it,’ we tell you ‘whoa, whoa, that has a vulnerability, but you’re never actually invoking that library, so you’re really not insecure,’ and that can cut the amount of work dramatically. LIke, three-quarters of the vulnerabilities those other tools report are false positives, so it’s really cuts the work.
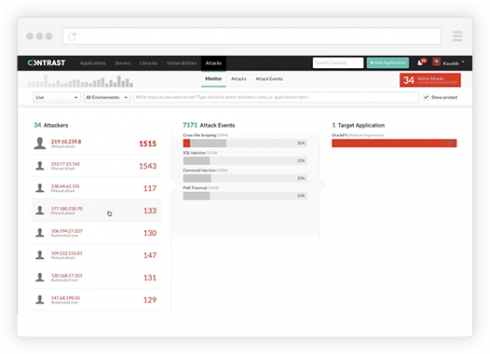
The last thing that we do, is extending right into production. We work there as well. In production, Contrast prevents vulnerabilities from being exploited. We do this from inside the running application, but we can prevent SQL injection, cross-site scripting and express language injection, and a whole bunch of other classes of vulnerabilities, because we can actually observe them inside the running application.
We’re not trying to guess whether they’re being attacked by looking at network traffic or HTTP requests or whatever. We’re actually watching the code run, seeing an exploit attempted, and preventing it from harming the application. So when you zoom out, we’re protecting the whole application process, from the first line of code all the way through production, all at the application layer. You still need to secure your operating system, your containers and your cloud environment. We don’t do that. We take care of the application layer.






