Smartwatch users might want to think twice about the information they plug into their wearable device, as a recent study from HP revealed a majority of these technologies have serious security flaws.
“Smartwatches have only just started to become a part of our lives, but they deliver a new level of functionality that could potentially open the door to new threats to sensitive information and activities,” said Jason Schmitt, general manager of HP Security and Fortify. “As the adoption of smartwatches accelerates, the platform will become vastly more attractive to those who would abuse that access, making it critical that we take precautions when transmitting personal data or connecting smartwatches into corporate networks.”
(Related: Smartwatches are not good at protecting your personal data)
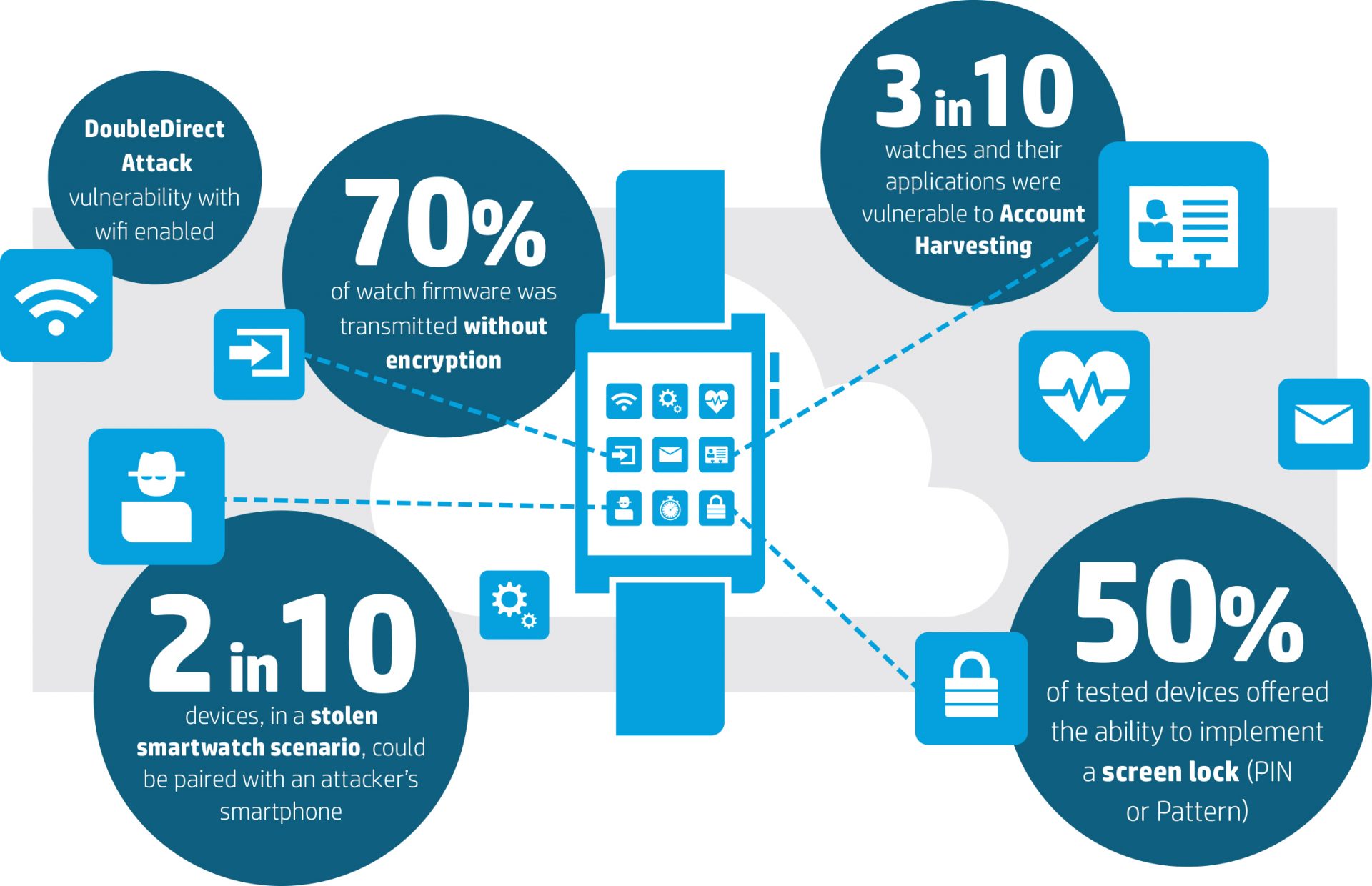
The company assessed 10 of the most popular smartwatches on the market, revealing that all of them had security flaws. One of the biggest problems was the collection of data and where that data was being sent. According to Daniel Miessler, lead researcher on the study and practice principal with HP Fortify, in 90% of the smartwatch cases, at least one connection was not encrypted.
“There were a lot of situations where encryption just wasn’t being used, and that combined with the data going out to multiple locations is a bit alarming,” he said. “When you purchase a smartwatch, you are not just getting the smartwatch; you usually get a mobile application and also often a cloud component. All these things are different attack surfaces to get you into what the watch has, so it is important to realize there are different ways to attack these ecosystems.”
The most common security issues found included insufficient user authentication and authorization, lack of transport encryption, insecure interfaces, insecure software/firmware, and privacy concerns. At the lowest level, HP was able to obtain personal identification information such as user names, passwords and location. But according to Miessler, the potential consequences of the security vulnerabilities could lead to more disruptive attacks.
“We believe smartwatches will be used increasingly for access control,” Miessler said. “We already have situations where you can get into a car, you can get into your front door at your home, or you can get into a hotel room just with your watch. As more and more access is sort of stacked onto the watch itself, it will become a more attractive target for attackers.”
The problem is that smartwatch manufacturers and software developers are not used to building things that go online, Miessler explained. “A lot of them are used to building things that used to be standalone, and were not really network or Internet connected, so it is a new type of exposure for them.”
To address this problem, Miessler said teams should ensure security is built in as part of the development process, TLS implementations are configured and implemented properly, user accounts and sensitive data are protected by strong passwords, and man-in-the-middle attacks are prevented.
According to him, the company is in the process of responsible disclosure, and cannot identify the tested smartwatches until the companies release a patch and gives authorization to talk about it.
The full report can be found here.






