Kubernetes security company Octarine has announced two new open-source projects designed to protect against cloud-native security vulnerabilities. The Kubernetes Common Configuration Scoring System (KCCSS) is a framework for rating security risks, and kube-scan is a workload and assessment tool.
“Our mission is to make the adoption of DevSecOps best practices simple, understandable, and achievable for any organization running Kubernetes,” said Julien Sobrier, head of product at Octarine. “One glaring blindspot is at the configuration level when building and deploying cloud native apps. We hope these two new projects benefit the Kubernetes practitioners industry-wide and look forward to collaborating with the community to make Kubernetes as secure and compliant as possible.”
RELATED CONTENT: CNCF introduces a Kubernetes bug bounty program
According to the company, KCCSS is similar to the Common Vulnerability Scoring System. The difference is KCCSS focuses on configuration and security settings. Configurations can be insecure, neutral or critical for protection and remediation, Octarine explained. The project is designed to score risks and remediations and then calculate risk for every runtime setting from 0 (no risk) to 10 (high risk). In addition, KCCSS shows the potential impact through confidentiality, integrity and availability.
“KCCSS makes it easy to talk about security across teams in your organization. DevOps teams can track the high risk workloads. Developers see what settings are impacting the security of their services, and can decide to either change those settings, or bring down the risk level to an acceptable level. Compliance or Business teams get a clear understanding of the potential impact of the risk and can decide whether it is acceptable or not,” the KCCSS GitHub page stated.
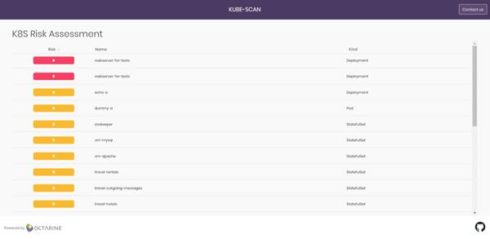
Kube-scan is based on KCCSS and analyzes more than 30 security settings and configurations including privilege levels, capabilities and Kubernetes policies. This helps the project establish a risk baseline and identity which workloads are at risk as well as why and what the consequences are. In addition, it prioritizes remediation and updates to Pod Security Policy, Pod definitions and manifest files. “With over 30 security settings under the control of every single developer, you need to be a Kubernetes expert to understand if the final configuration introduces a high risk to your cluster. With a single change to a single file, you can open your entire Kubernetes cluster to attacks, leak secrets, risk confidential data, or accidentally give public access to private services,” the company wrote.