BlackBerry announced new efforts to fight against cybersecurity attacks at this week’s Black Hat USA 2020 conference. The company’s new open-source tool PE Tree is designed to significantly reduce the time and effort required to reverse engineer malware.
According to the company, with the use of PE Tree, reverse engineers can view portable executable (PE) files in a tree-view using pefile and PyQt5. This lowers the bar for dumping and reconstructing malware from memory while providing an open-source PE viewer code-base that the community can build upon, BlackBerry said in its announcement.
RELATED CONTENT: It’s critical to keep your open-source components up to date and secure
The tool integrates with HexRays’ IDA Pro decompiler to provide easy navigation of PE structures, as well as dumping in-memory PE files and performing import reconstruction; critical in the fight to identify and stop various strains of malware.
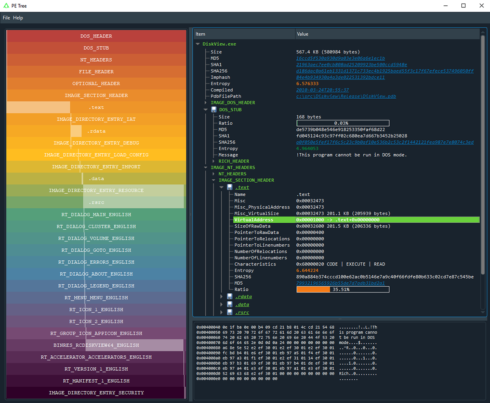
PE files are parsed using Ero Carrera’s pefile module before being mapped into a tree-view. There, users can view a summary of headers including MZ header, DOS stub, rich headers, data directories, and many more.
Then, a left-hand “rainbow view” offers a high-level overview of the PE file’s structure, as well as conveying the offset/size/ratio of each region.
Finally, each region can be clicked to jump to in the tree-view, or right-clicked to save to file or export to CyberChef.
“As cybercriminals up their game, the cybersecurity community needs new tools in their arsenal to defend and protect organizations and people,” said Eric Milam, the vice president of research operations at BlackBerry. “We’ve created this solution to help the cybersecurity community in this fight, where there are now more than 1 billion pieces of malware with that number continuing to grow by upwards of 100 million pieces each year.”
PE Tree is developed in Python and supports the Windows, Linux and Mac operating systems. It can be installed and run as either a standalone application or an IDAPython plugin.






