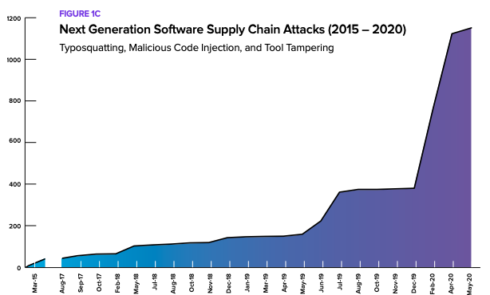
The past year saw a 430% increase in next-generation cyber attacks aimed at actively infiltrating open source software supply chains, according to the 2020 State of the Software Supply Chain report.
In the past 12 months, 929 next-generation software supply chain attacks were recorded. By comparison, 216 such attacks were recorded between February 2015 and June 2019.
“Following the notorious Equifax breach of 2017, enterprises significantly ramped investments to prevent similar attacks on open-source software supply chains,” said Wayne Jackson, the CEO at Sonatype. “Our research shows that commercial engineering teams are getting faster in their ability to respond to new zero-day vulnerabilities. Therefore, it should come as no surprise that next-generation supply chain attacks have increased 430% as adversaries are shifting their activities ‘upstream’ where they can infect a single open-source component that has the potential to be distributed ‘downstream” where it can be strategically and covertly exploited.”
Next-generation software supply chain attacks involve the intentional targeting and compromising of “upstream” open-source projects so that attackers can then exploit vulnerabilities when they inevitably flow “downstream,” according to Sonatype.
In 2019 Darmstadt University researchers found that 391 highly influential project contributors affect more than 10,000 components through their complex web of dependencies. If an adversary were to gain access to one of these maintainers, this could dramatically widen the impact of their attack.
These types of attacks include Octopus Scanner, which affected 26 open-source projects on GitHub and targeted the tools developers were using to build their code; and electron-native-notify, which focused on getting a malicious package into a build chain.
Currently, the most common type of attack is Typosquatting, an indirect attack vector that preys on developers making otherwise innocent typos when searching for popular components. If developers accidentally type in a wrong name, they might accidentally install a malicious component of a similar name.
Another common attack is Malicious Code Injection, which is carried out through a variety of means, including stealing credentials from a project maintainer.
According to the report, these next-gen attacks are possible for three main reasons.
One is that open-source projects rely on contributions from thousands of volunteer developers, making it difficult to discriminate between community members with good or bad intentions.
Secondly, the projects incorporate up to thousands of dependencies that may contain known vulnerabilities. Lastly, the ethos of open source is built on “shared trust,” which can create a fertile environment for preying on other users, according to the report.
On the other hand, legacy software supply chain attacks involve waiting for new zero-day vulnerabilities to be publicly exposed and then taking advantage of them before they can be fixed. The study found that 51% of organizations require more than a week to remediate new zero-day vulnerabilities.
The report found that to fix these issues, teams that are investing more in software composition analysis (SCA) open-source automation capabilities are able to handle the issues faster.
High performing development teams are 26 times faster at detecting and remediating open-source vulnerabilities, and deploy changes to code 15 times more frequently than their peers.
They are also 59% more likely to use automated software composition analysis (SCA) and are almost 5 times more likely to successfully update dependencies and to fix vulnerabilities without breakage.
“It was really exciting to find so much evidence that this much-discussed tradeoff between security and productivity is really a false dichotomy. With the right culture, workflow, and tools development teams can achieve great security and compliance outcomes together with class-leading productivity,” said Dr. Stephen Magill, the principal scientist at Galois and the CEO of MuseDev.






