GitHub announced a new feature for Dependabot alerts that helps developers see how vulnerabilities affect their code.
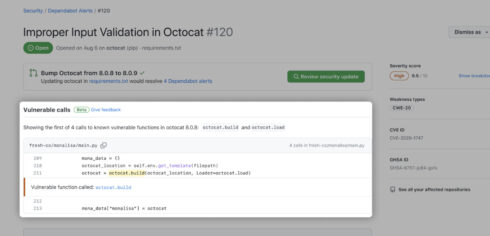
Dependabot alerts use GitHub’s precise code navigation engine to determine if a repository directly calls a vulnerable function.
The new feature marks a shift in how GitHub curates information on vulnerable packages from the Advisory Database to curating information on affected functions for each source library.
GitHub performs static analysis with functions in order to generate an affected call graph for a repository, which surfaces on a Dependabot alert.
The implementation is powered by stack graphs, which powers Precise Code Navigation and provides a no-configuration experience that works on any advisories with annotated vulnerable functions, according to GitHub.
GitHub announced that it has details of vulnerable functions for 79 Python advisories from the pip ecosystem and that it will continue backfilling data on vulnerable functions for Python advisories through the beta, as well as supporting any new Python advisories.
“Since our February ship of improvements to Dependabot alerts, Dependabot has helped developers resolve nearly 3 million alerts,” Erin Havens, product manager at GitHub, wrote in a blog post. “Dependabot alerts will now surface whether your code is calling vulnerable code paths, so that you can prioritize and remediate alerts more effectively.”






