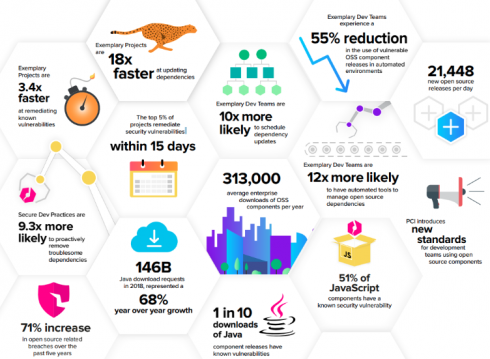
While open-source software is an integral part of software development today, security continues to be an issue. A recently released report revealed a 71 percent increase in open-source security related breaches over the last five years. In addition, 25 percent of organizations reported a confirmed or suspected open-source software related breach.
RELATED CONTENT: Open source at 20: The ubiquity of shared code
The fifth annual Sonatype State of the Software Supply Chain Report is based on patterns and cybersecurity hygiene practices of about 36,000 open-source projects and 3.7 million open-source component releases.
According to Derek Weeks, VP at Sonatype, one of the reasons security is still such a problem with open-source projects is because developers treat open-source software as if they were created equal. “This year’s report definitely shows that we can’t do that, we can’t treat all open source projects as equal. It has long been believed that in the realm of open source development, ‘with more eyeballs, all bugs are shallow.’ In other words, the more popular open source components were, the fewer bugs or vulnerabilities they might have. That’s just not true – and it leads to a false sense of security,” he said.
When looking at behavior patterns and best practices the report looked at differences between how projects update dependencies and fix vulnerabilities; how components are used; and what advice can be offered from how those components are consumed. The report found only 5 percent of projects remediate security vulnerabilities within 21 days; “exemplary” projects such as Elasticsearch, Mulesoft, and SonarSource are 3.4 faster at remediating known vulnerabilities and secure development practices are 9.3 times more likely to remove troublesome dependencies.
“Our research into popularity of components in this year’s report distinctly shows that developers should not select components based on popularity alone. While many of the best quality open source components are popular, not all popular open source projects release improvements or remediate vulnerabilities frequently. Some of the most popular components may take 200 days or more, on average, to release new updates or remediate known security vulnerabilities,” said Weeks.
In order to improve and ensure open-source security, Weeks suggests creating a Software Bill of Materials (SBOM) that will help enterprise developers better understand their software supply chains. The SBOM will give developers observability and insight into the open source software components their teams are using, known security vulnerabilities, license risks and architectural risks. “You cannot manage what you cannot see,” he said.
In addition to a SBOM, development teams should use a repository manager, regularly update dependencies, use the most recent versions of components, and automate.
“If developers better understood what suppliers (projects) they were using and focused on only using the best kind — and recognizing that they’re not all equal – it would be a huge step toward forward,” said Weeks.
Weeks also adds Median Time to Update (MTTU) can be a critical metric when deciding what component to use. “Rapid MTTU is associated with lower security risk and is also more accessible from public sources than other metics enterprises might want to rely upon such as vulnerability data,” he said. Open-source project maintainers can also use MTTU to help enterprise ensure security. “Developers maintaining OSS projects who are considering adding a new dependency, and looking for a metric to guide that choice, would do well to focus on those dependencies with fast MTTU. Since remediating a vulnerable dependency typically involves upgrading to a new dependency version, components with fast MTTU values naturally exhibit faster response to dependency vulnerabilities,” Weeks explained.
Another key finding of the report revealed velocity shouldn’t and doesn’t have to come at the cost of security. “We found that exemplary open source project initiatives benefit tremendously from higher code commits, release frequencies, and to some extent larger development teams,” said Weeks.
Other findings of the report include a 68 percent year over year growth in download requests of Java components; 21,448 new open-source releases are available to developer every day; and a 55 percent reduction in the use of vulnerable open-source components from top enterprise development teams.
“I think it’s important for developers to understand that secure coding practices can actually speed up their process and increase innovation. In order to survive and thrive in today’s application economy the best development teams are actively embracing open source innovation, dependency management practices, and automated tooling for open source governance,” said Weeks.






