Researchers from Microsoft and Cisco Talos have found a new fileless malware strain dubbed Nodersok by Microsoft or Divergent by Talos.
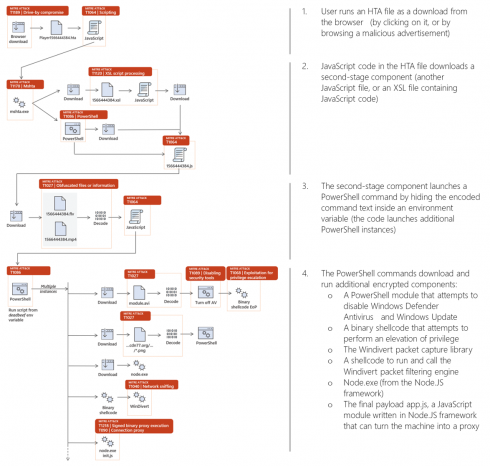
The malware leverages the popular Node.js framework (which has not often been used for such attacks) used by many Web applications and WinDivert, a network packet-capture and manipulation utility, to turn the systems into unwitting proxies. The malware most commonly comes from compromised advertisements that deliver HTML application files, each under a different name, Microsoft explained.
“Nodersok went through a long chain of fileless techniques to install a pair of very peculiar tools with one final objective: turn infected machines into zombie proxies,” Microsoft wrote in a post. “While the file aspect of the attack was very tricky to detect, its behavior produced a visible footprint that stands out clearly for anyone who knows where to look.”
The attack uses a randomly named domain that typically doesn’t last for more than a day or two. After it downloads an XSL or JavaScript, it contacts the remote command and control domain to download an RC4-encrypted MP4 file. This file then starts Powershell.
Powershell then attempts to disable Windows Defender Antivirus, disable Windows updates and run binary shellcode that attempts elevation of privilege. It also drops a JavaScript payload written for the Node.js framework that turns the device into a proxy
According to the researchers, most of the instances of this malware were found in the United States at 60 percent, followed by the United Kingdom at 21 percent. The sectors most affected were education at 42 percent, business and professional services at 8 percent, followed by both the healthcare and financial sectors at 7 percent. A vast portion of the attacks happened in September.
“The malware loader described is currently under active development. Talos has observed multiple versions of the loader being used to install the Divergent malware. Attackers are attempting to monetize these infections through the use of click fraud,” Cisco Talos researchers wrote in a blog post. “The threat landscape is constantly evolving as attackers test new techniques and methodologies to maximize their revenue generation capabilities. Organizations should be aware of these changes and ensure that their security programs are able to remain effective against these changing tactics, techniques, and procedures.”