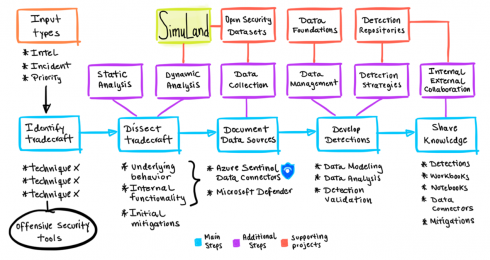
Microsoft announced a new open-source initiative, SimuLand, to help security researchers deploy lab environments that reproduce well-known techniques used in attack scenarios.
Participants can use the labs to then test the effectiveness of Microsoft 365 Defender, Azure Defender, and Azure Sentinel detections.
The simulation steps are mapped to detection queries and alerts to the aforementioned technologies.
Threat research will be extended after each simulation exercise through the use of elementary and forensic artifacts generated after each scenario. Every simulation plan provided through this project is research-based and broken down into attacker actions mapped to the MITRE ATT&CK framework, according to Microsoft.
“Our goal is to have SimuLand integrated with threat research methodologies where dynamic analysis is applied to end-to-end simulation scenarios,” Roberto Rodriguez, a threat researcher at MSTIC R&D wrote in a blog post.
Microsoft plans to use SimuLand to identify mitigations and attacker paths by documenting preconditions, expedite the design and deployment of threat research lab environments and stay up to date on the latest techniques that are used by attackers.
SimuLand offers lab guides to prepare and deploy the lab environment and to execute the end-to-end simulation exercise, an initiative which stems from the open-source projects Azure Sentinel2Go and Blacksmith from the Open Threat Research (OTR) community.
The labs replicate either hybrid cross-domain or cloud environments depending on the simulation.
Microsoft said it’s working to expand the project by possibly adding a A data model to document the simulation steps, a CI/CD pipeline with Azure DevOp, the automation of attack actions and more.






