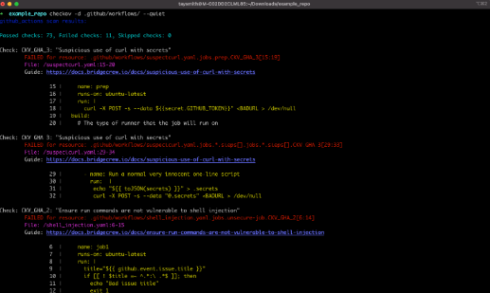
Checkov, the open-source tool for finding infrastructure misconfigurations, has been updated with new CI/CD configuration policies. These policies can be applied across popular CI/CD frameworks like GitHub Actions, GitLab Runners, BitBucket Pipelines, CircleCI, and Argo.
Checkov has a developer-first approach to supply chain security, so it embeds these CI/CD policies directly into existing DevOps workflows to make it easier for developers to adopt them.
Industry benchmarks, such as SLSA and CIS, were used to create these policies. According to the Checkov team, this helps developers align their pipelines with industry standards.
The new policies include controls like requiring two reviewers for a pull request, requiring signatures for individual commits, preventing deprecated commands or beta features from being used, preventing secrets exfiltration, and blocking privileged workflow pods.
According to the Checkov team, CI/CD security policies are particularly needed to prevent supply chain attacks. They explained that CI/CD pipelines that aren’t properly secured provider attackers with an easy entry point into the software supply chain.
As an example, a repository configured to run any command in a pull request can be manipulated by injecting code that will send API tokens and other secrets to the attacker, the team explained.






