The software reliability company Gremlin announced three major platform updates at the Virtual KubeCon North American 2020 conference this week to ensure users can safely and securely prepare solutions for failure regardless of the Kubernetes platform. The new features are: the ability to isolate its resource attacks into a single container, support for containerd and CRI-O container runtimes, and fine-grained namespace access control.
“Kubernetes is becoming the default way to build and operate applications at many enterprises, but along with the advantage of abstraction comes uncertainty,” said Lorne Kligerman, senior director of product at Gremlin. “We’re providing DevOps teams with better tooling to understand how their Kubernetes applications will behave under various stresses, such as when a neighboring container is spiking with traffic.”
RELATED CONTENT:
The First 5 Chaos Experiments to Run on Kubernetes
To build resilient systems, embrace the chaos
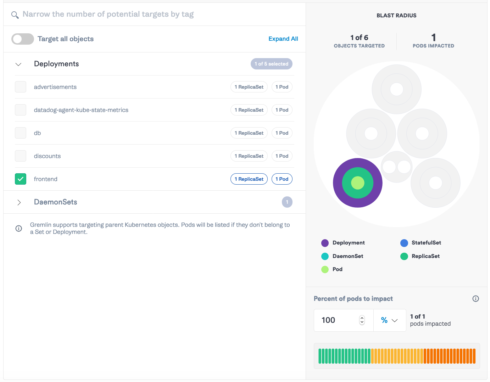
According to Kligerman, because Kubernetes enables a higher tenant density on a host and increases infrastructure utilization, it can result in a “noisy neighbor” problem for DevOps teams. For instance, scaling or problematic services can impact one another if they are in the same cluster. “If applications aren’t tested for HPA and resource limits, it’s difficult to determine if your application is decoupled enough to scale out pods independently and to know if noisy neighbors can still break services sharing the same node,” Kligerman wrote in a post.
By isolating its resource attacks into a single container, users can test individual pod scaling and resource limits, and prevent “noisy neighbors.”
The noisy neighbor problem can also result in security and access control concerns. The new fine-grained namespace access control aims to address this by ensuring only team members with correct permissions have access to specific Kubernetes objects. “This is crucial to ensuring the Chaos Engineering work an engineer is doing isn’t negatively impacting neighboring services,” the company stated in its announcement.
Lastly, support for the container runtimes containerd and CRI-O is making chaos engineering available on more platforms. The company also supports earlier versions of Amazon EKS and OpenShift, and added support for new container runtimes to be able to support the latest versions.
“By supporting these additional runtimes, customers can now run attacks across their environment, even if it’s mixed, using a single UI and API. This makes testing heterogeneous environments even easier,” Kligerman explained.






