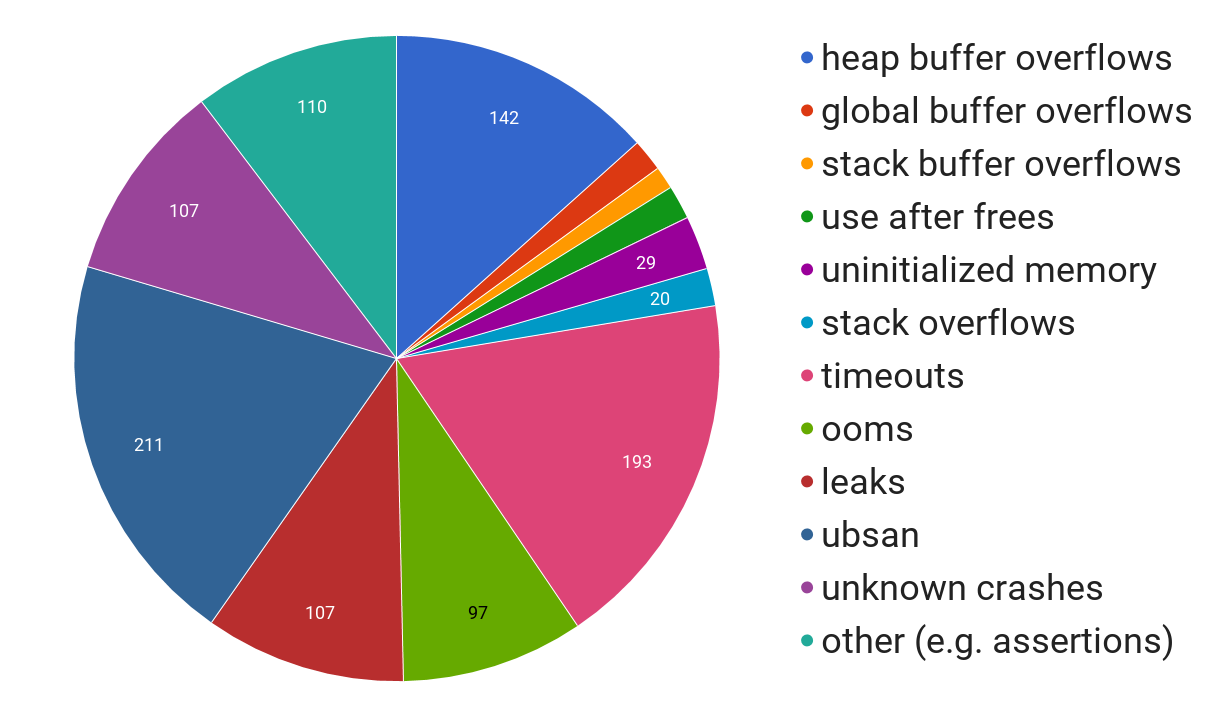
Google released OSS-Fuzz five months ago with a mission to make open-source projects stable, secure and reliable. Since then, the continuous fuzzing solution has found more than 1,000 bugs with 264 of them flagged as potential security bugs.
“OSS-Fuzz has found numerous security vulnerabilities in several critical open source projects: 10 in FreeType2, 17 in FFmpeg, 33 in LibreOffice, eight in SQLite 3, 10 in GnuTLS, 25 in PCRE2, nine in gRPC, and seven in Wireshark, etc. We’ve also had at least one bug collision with another independent security researcher (CVE-2017-2801),” a team of software security engineers at Google wrote in a post.
OSS-Fuzz is designed to catch issues after a regression is introduced and before users are impacted. It detects memory safety related bugs, correctness or logic bugs as well as timeout and out-of memory failures.
In order to expand its open-source security efforts, Google is announcing new rewards for open-source projects. “We believe that user and internet security as a whole can benefit greatly if more open source projects include fuzzing in their development process. To this end, we’d like to encourage more projects to participate and adopt the ideal integration guidelines that we’ve established,” the team wrote.
The company’s existing Patch Rewards program is being expanded to include fuzz targets rewards. Eligible projects will receive up to $1,000 for initial integration and up to $20,000 for ideal integration.
According to Google, ideal integration includes fuzz targets checked into upstream repository, fuzz targets provide good code coverage, fuzz targets are a part of the official upstream development and regression testing process, and integrated in the build system.