Google launched Open Source Vulnerabilities (OSV) this week to provide users with precise data on where a vulnerability was introduced, where it got fixed, and to help users know if they’ve been impacted.
According to Google, OSV solves issues surrounding open-source security using automation in two key ways: improving the accuracy of vulnerability queries and reducing the work required by maintainers to publish vulnerabilities.
Previously, developers have struggled to map vulnerabilities such as those identified as Common Vulnerabilities and Exposures (CVE) because versioning schemes in existing vulnerability standards don’t map well with open-source versioning schemes, according to Oliver Chang and Kim Lewandowski from the Google Security Team in a blog post.
It’s also very time consuming for maintainers to find out which versions were affected and to track all of the commits across all of their branches for downstream consumers after vulnerabilities are fixed.
“Many open source projects, including ones that are critical to modern infrastructure, are under-resourced and overworked. Maintainers don’t always have the bandwidth to create and publish thorough, accurate information about their vulnerabilities even if they want to,” Chang and Lewandowski wrote.
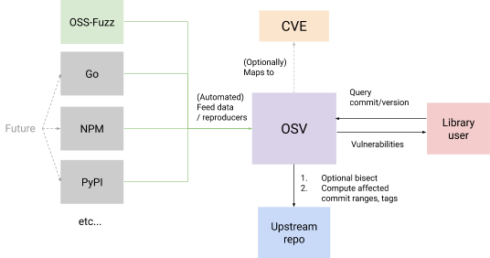
OSV’s automation capabilities simplify vulnerability reporting by accurately determining the list of affected versions and commits. If that information is not available, OSV requires providing a reproduction test case and steps to generate an application build.
It then uses bisection, a method used to identify change sets that result in a specific behavior change to find these commits through automation. OSV then automates the triage workflow for an open source package consumer by providing an API to query for vulnerabilities, the Google Security team explained.
Google is planning to work with open-source communities to extend with data from various language ecosystems such as NPM and PyPI, and to work out a pipeline for package maintainers to be able to submit vulnerabilities in a simplified way.
“Our goal with OSV is to rethink and promote better, scalable vulnerability tracking for open source. In an ideal world, vulnerability management should be done closer to the actual open source development process, aided by automated infrastructure,” Chang and Lewandowski wrote. “Projects that depend on open source should be promptly notified and fixes uptaken quickly when a vulnerability is reported.”