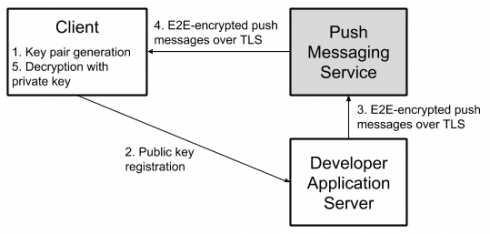
Google is trying to make it easier to implement end-to-end (E2E) encryption with the release of Project Capillary. The open-source library is designed to simplify the implementation of E2E-encryption for push messages between developer servers and users’ Android devices.
“Developers already use HTTPS to communicate with Firebase Cloud Messaging (FCM). The channel between FCM server endpoint and the device is encrypted with SSL over TCP. However, messages are not encrypted end-to-end (E2E) between the developer server and the user device unless developers take special measures,” Giles Hogben, privacy engineer, and Milinda Perera, software engineer for Google, wrote in a post.
The library also includes functionality for sending messages that are only able to be decrypted on recently unlocked devices. According to Google, this is so that it can support decrypting messages on devices that use File-Based Encryption, which is when encrypted messages are cached in Device Encrypted storage and then message decryption keys are stored in Android Keystore. This enables developers to specify messages with sensitive content and then have them remain encrypted in a cached form until the user unlocks and decrypts their device.
The library also handles crypto functionality and key management across Android version as far back as KitKat, key generation and registration workflows, message encryption and decryption, integrity protection to prevent message modification, and caching of message received in unauthenticated contexts to later be decrypted and displayed after unlocking the device.
Project Capillary supports edge-cases, including users that add or reset the device lock after installing the app, or users resetting app storage.
According to the company, the library supports RSA encryption with ECDSA authentication and Web Push encryption. This enables developers to re-use existing server-side code that was developed for sending E2E-encrypted Web Push messages to browser-based clients.