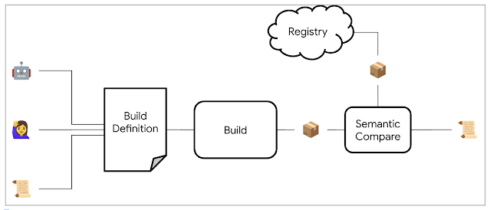
Google is hoping to improve public trust in open source projects with the launch of a new open source project called OSS Rebuild that reproduces upstream artifacts and compares the new package with the original artifact.
According to Google, this process enables customers to verify a package’s origin, understand and repeat its build process, and customize the build.
“Our aim with OSS Rebuild is to empower the security community to deeply understand and control their supply chains by making package consumption as transparent as using a source repository,” Matthew Suozzo from the Google Open Source Security Team (GOSST) wrote in a blog post.
It can detect several types of supply chain compromise, such as source code not present in the public source repository being in published packages, build environment compromise, or stealthy backdoors, such as was seen with XZ Utils.
The project itself consists of an automated process for getting declarative definitions for existing packages, SLSA Build Level 3 provenance, build observability and verification tools that can be integrated into vulnerability management workflows, and infrastructure definitions so that users can run their own instances of OSS Rebuild.
Initially, OSS Rebuild supports Python, JavaScript/TypeScript, and Rust package registries: PyPI, npm, and Crates.io. It offers rebuild provenance for several of the most popular packages in those languages. Google implied in its blog post that it plans to extend OSS Rebuild to more package registries in the future.
“Our vision extends beyond any single ecosystem: We are committed to bringing supply chain transparency and security to all open source software development,” Suozzo wrote.